It’s not often I get to step back from day-to-day work items and pause to think about something. I’ve had a Lenovo X1 ThinkPad Nano since Tuesday, February 23 (I wrote a First Look piece the next day). Since then, I’ve worked with that machine daily. I’ve even used it in place of my iPad Air for evening reading in bed. All this has me pondering Lenovo ThinkPad X1 Nano further. I want to position and present it properly to readers so they can decide if what it offers is what they want. . . and if they want to pay for it, too.
When Pondering Lenovo ThinkPad X1 Nano, Use Cases Rule
To justify the cost, one really needs strong use cases for a thin-and-light laptop. It weighs 381g more than my iPad (906 vs 525g). But it’s still comfortable on my lap. As a pretty serious touch typist, I actually prefer constant access to a keyboard. I do now wish, though, that Lenovo offered a touchscreen option for the X1 Nano for simple tablet-friendly activities like web surfing and reading e-books.
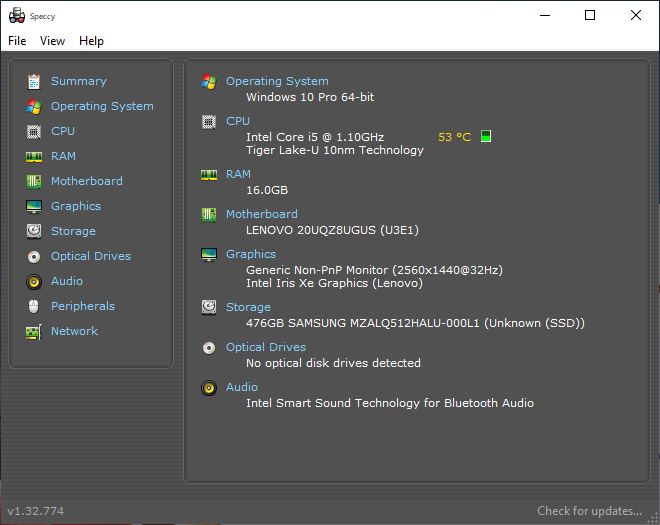
Over time, I’ve grown even more impressed with the X1 Nano’s performance and capability. It really does run on par with my older (2016) desktop PC. That’s true despite 32GB RAM and an i7-6700 on that PC vs. 16GB RAM and an i5-1130G7 on the X1 Nano. To me, it’s a telling illustration of how fast technology marches ahead. I didn’t expect an i5 to be able to go head-to-head with an i7 (even a 5-year-old model).
Blast from the Past…
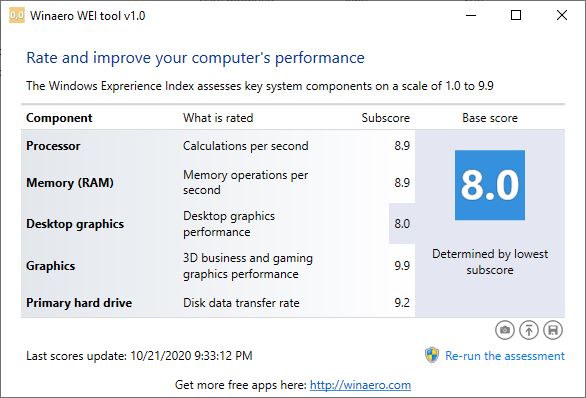
The lead-in graphic for this story comes from Sergey Tkachenko’s WEI clone. He calls it the Winaero WEI Tool. For those who don’t remember — or who never knew — WEI stands for Windows Experience Index. It’s been around Windows since Vista came out in 2007. You can still run the equivalent functionality in Windows 10, in fact, with this command winsat formal. I like the Winaero tool because it presents the same look’n’feel as in Vista and 7.
What you see in that graphic is a rough-and-ready assessment of hardware components on the PC it’s run on. Those numbers show values from 8.9 (CPU, RAM) to 9.2 for the SSD and 9.9 for 3D business and gaming graphics. The only outlier is the desktop graphics — Iris Xe in this case — which come in at a relatively low 8.0 value (the primary reported value as well, because WEI uses the lowest number to desigate overall capability).
FWIW, the only area in which my older desktop beats the X1 Nano is on the desktop graphics category (it’s got an NVIDIA GTX 1070 card). All the other metrics are within 0.1 of one another, so neither machine obviously beats the other by any kind of margin.
Desktop graphics performance notwithstanding, I’ve come to appreciate the X1 Nano quite a bit in the 10 days I’ve had it in hand. It runs acceptably when surfing the Web, using Outlook or Word (my two most frequently used and important desktop apps). To be honest, I am seriously considering buying one of these with my own money. I can’t give a laptop a better endorsement than that.
What’s the Ideal Package?
If you, like me, decide to buy the ThinkPad X1 Nano, I recommend buying the i7 model with the 16 GB RAM configuration. Because the SSD is the only user serviceable part (RAM is soldered), get the 256 GB SSD, which you’ll want to replace when something like the Sabrent 1TB Rocket 4 becomes available in a 2242 form factor.
If you absolutely have to buy something now, the Sabrent 1 TB Rocket is available in a 2242 package. While it’s a bit slower than the Rocket 4, it’s faster than the Samsung OEM parts Lenovo uses in the Nano. You’ll also want to buy a Thunderbolt/USB-C dock, because the Nano is pretty short on ports (2xThunderbolt + 1xheadphone is all you get). As a backup fiend, I’ve already got a 5TB 2.5″ drive enclosure hooked up for extra storage and Macrium Reflect’s use.