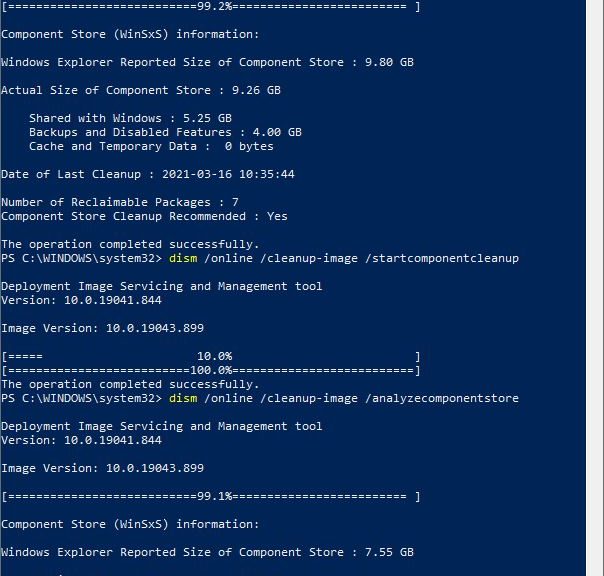
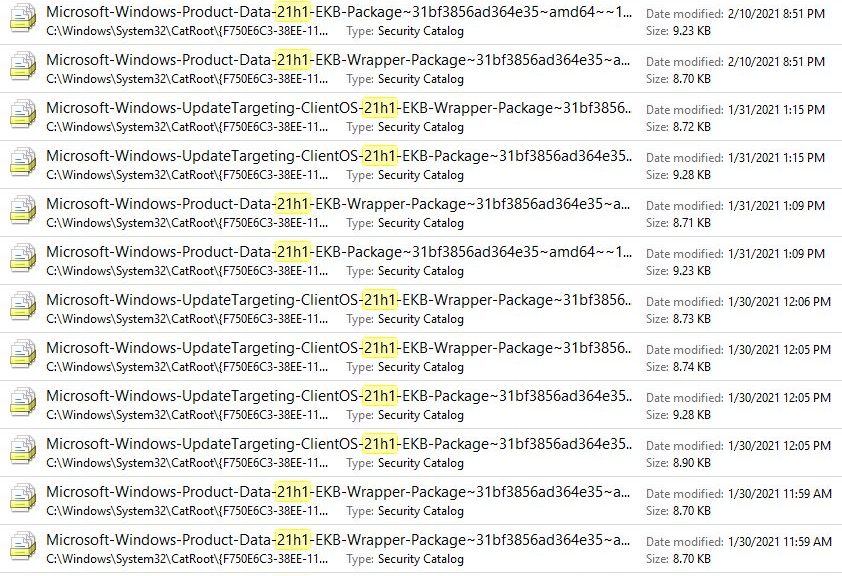
I’m running the Beta Channel Insider Preview on my Surface Pro 3. I just bumped it to Build 19043.899 thanks to KB5000842. Out of curiosity, I then ran the DISM commands to analyze and clean up the component store as shown in the lead-in graphic for this story. A final analyze shows interesting partial 21H1 component store cleanup occurred. Let me explain…
What Does Interesting Partial 21H1 Component Store Cleanup Mean?
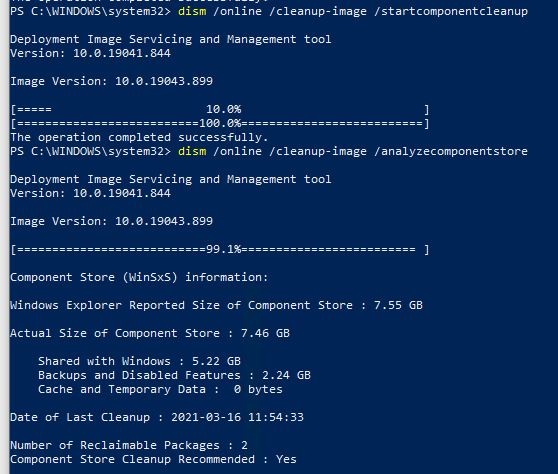
If you take a look at some detail from the lead-in graphic then check the screencap below, you’ll see they show 7 reclaimable packages before clean-up. After cleanup, 2 reclaimable packages still remain behind.
Notice that 2 reclaimable packages persist, event after running the cleanup option.
Reclaimable packages persist after dism cleanup for one of two reasons AFAIK:
1. At some point, the user ran the /resetbase parameter in an earlier dism cleanup.
2. Something odd or interesting is going on in the component store, and dism can’t clean up one or more packages (in this case, two).
I don’t use /resetbase on test machines as a matter of principle. So something interesting and odd is going on here.
Another Try Produces No Change
Having seen this before on other Insider Previews (and production Windows 10 versions), I had an inkling of what would happen. I repeated the cleanup and got the same results: 2 reclaimable packages still show. In my experience, this means they’re “stuck” in the component store. What I don’t know is if taking the image offline and trying again would make any difference. What I do know is that this won’t change until Microsoft finalizes the 21H1 release for general availability (or issues a specifically targeted fix).
Trading on my connections with the Insider Team at MS, I’ll be letting them know about this curious phenomenon. We’ll see if anything changes as a result. My best guess is that this gets a cleanup as part of the final release work sometime in the next 2-3 weeks. That said, only time will tell. Stay tuned!