Right now, I have two PC dedicated to Windows 11 testing and learning. Just recently, I discovered some vexing Windows 11 Antimalware platform update issues. The short version is: one of my PCs is up-to-date. It’s no longer subject to Automatic Sample Submission reset to off following each restart. Alas, the other remains stubbornly stuck on an earlier Antimalware platform release. None of the update options available work, so I can’t get no relief. Let me explain…
Fighting Vexing Windows 11 Antimalware Platform Update Issues
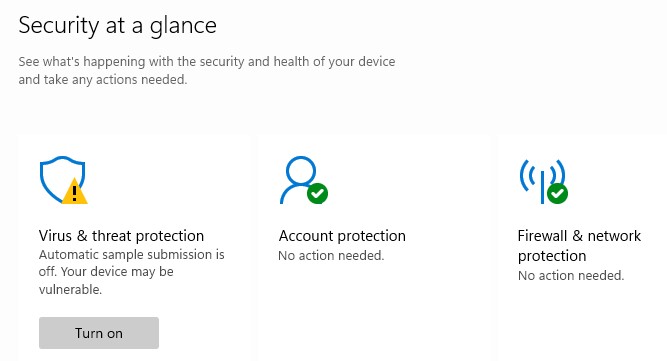
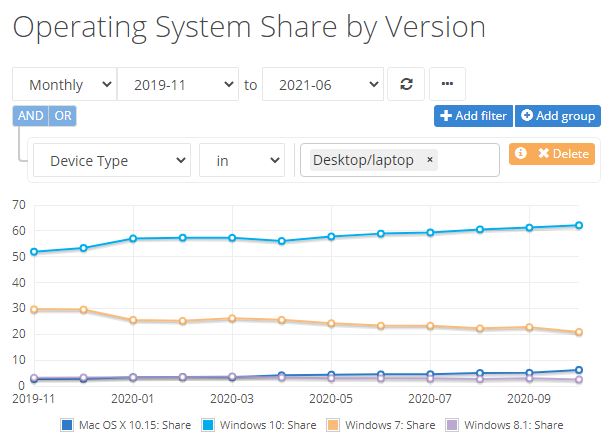
First, let me be clear. This is a known and documented Windows 11 issue. It’s been around since the initial release hit. Indeed, a fix exists: when the Antimalware Platform version gets to 4.18.2107.4 or higher, the problem disappears. For the record that problem is depicted in this story’s lead-in graphic. After every reboot, the Automatic Sample Submission feature for virus uploads in Defender is turned off. The feature is easy to turn back on, until the next reboot. OCD OS maintainer that I am, the workaround isn’t enough for me. I want it fixed, for good, now.
Here’s the vexing part. WU hasn’t yet deigned to update the antimalware engine behind the scenes. Ditto for the Protection updates option in Windows Security. There’s a registry hack documented on a related ElevenForum thread. There’s even a manual Defender update download that’s supposed to take the Antimalware engine release to 1.2.2107.02. It comes in a file named defender-update-kit-x64.zip. Alas, inspection of said update file shows the Antimalware engine to be 4.18.2015.5. It’s too old to fix the issue, in other words. Thus, no relief just yet, shy of a permanent registry hack.
The Perils of Perfectionism
Yes, I could hack the registry to turn this off. But I’d have to unhack it again when the fix finally shows up on the X380 Yoga that’s affected. I’m going to have to wait for WU to get around to providing me the latest antimalware engine on its own, or find a newer manual update. Alas, that’s the way things go sometimes, here in Windows-World. Oddly, I find myself hoping for a new Windows 11 build, in hopes the latest antimalware engine will be part of its contents. Stay tuned: I’ll let you know how all this shakes out.
Note Added August 4: Update Came!
Thanks to long-time and active TenForums and ElevenForum user @Cliff S, I learned this morning that Antimalware Client Version 4.18.2107.4 arrived via WU. Checking my own previously stuck test machine, I saw it too, had gotten this update. And now, my PC no longer reverts to Automatic Sample Submission=Off after each reboot. Fixed!
I’ve also determined this version is available through the Microsoft Update Catalog. Search for KB4052623, and grab the correct version, if WU doesn’t come through for you.