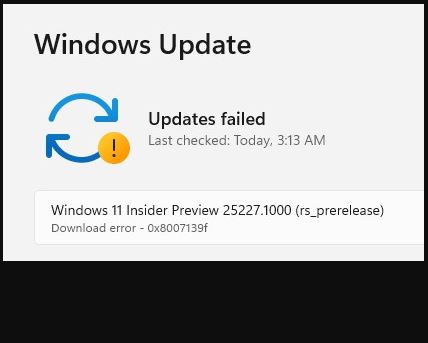
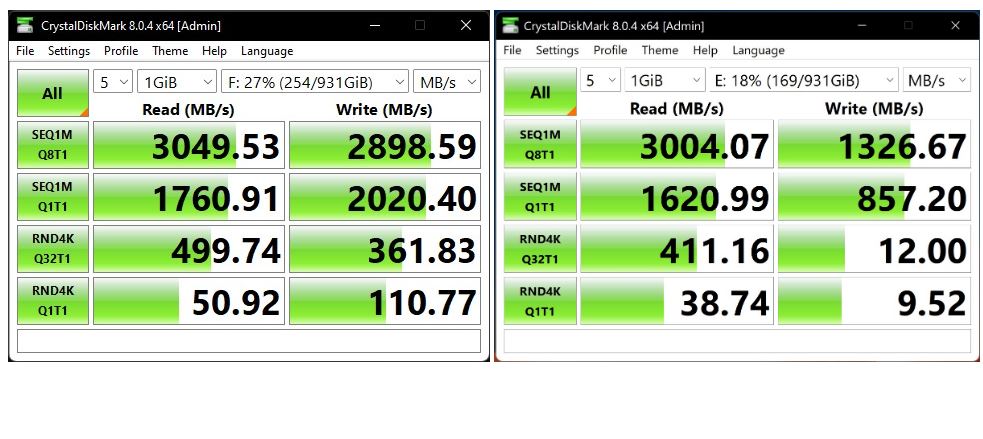
KB5018496 is out as of October 25. It takes production-level Windows 11 22H2 systems to Build 22621.755 when applied. To be fair, it’s a Preview CU, so not entirely cooked yet. But I observe that KB5018496 lands poorly so far because
(a) I don’t see any of its cool gradual rollout features on any of my PCs (e.g. right-click in Taskbar to launch Task Manager)
(b) When I attempted to explore the new Microsoft Accounts (MSA) capabilities, it crashed when I attempted to open the P16’s camera. I know that works because I use camera-based Hello to log onto that machine and had just done so minutes before. Sigh.
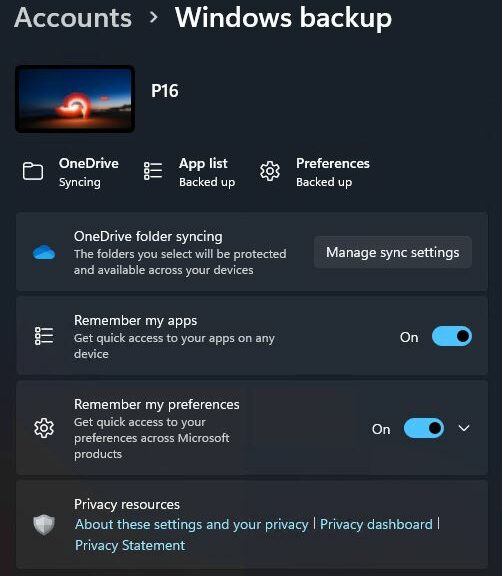
(c) I was unable to verify my identity in Settings → Accounts, because of the camera issue, so also unable to backup my MSA data. Sigh again.
Again: this is a preview release. And I’m qvetching about gradual rollout elements that either haven’t made it to my PCs, or that aren’t yet working as they should be. It’s a kind of “business as usual” thing, I guess.
What KB5018496 Lands Poorly So Far Really Means…
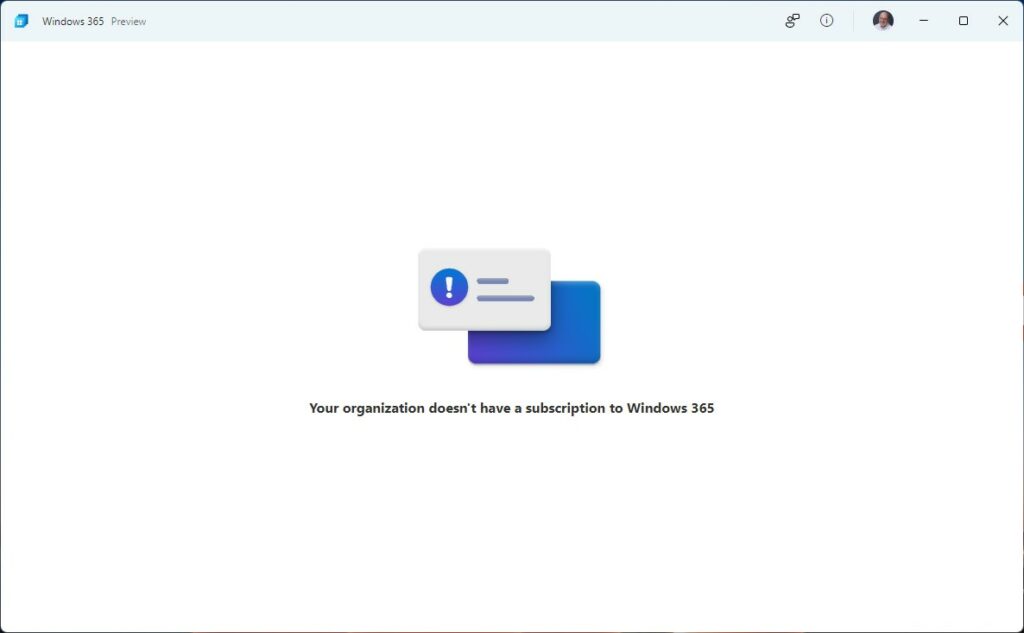
It’s pretty much par for the course that a few rough edges will show up in a preview release. Thus, for example, when I went to Accounts → Windows backup in an RDP session, the PC “knew” it couldn’t use the camera for validation. So I got an email to my MSA address instead. That worked just fine. The relevant screencap appears as the lead-in graphic for this story.
I assume there’s some kind of driver hiccup with the camera when logged in directly. It threw an error code that pointed squarely in that direction. That should be easy to run down and fix, so I’ll report it to Feedback Hub later today.
I’ve been using the right-click access to Task Manager in the taskbar on Insider versions of 22H2 for a while now. Thus, I also know it’s just a matter of time before it, too, shows up in production versions of 22H2.
Self-Inflicted Wounds? Perhaps…
So why do I install previews on production PCs? Because I’m an Insider and it’s my job to take such stuff on, and report what I see and find. I make daily image backups on those PCs, so the worst that can happen is a rollback to the previous image. I don’t generally do real work on those PCs unless I’m on the road. And in that situation, I probably wouldn’t mess with a preview because I wouldn’t want to lose the time (or the work done) since the last backup anyway.
And that’s how things go here in Windows World. Stay tuned for further developments. I’ll qvetch some more another day, for sure!