In refreshing my recollection of what I thought was called “Berkeley’s paradox” — but isn’t — I have to raise the question: If a Windows PC throws an Xbox error and you don’t use an Xbox, does it really matter? In my case, the answer is a resounding “No!” Thus when handling inconsequential Windows errors: remove or ignore are my primary strategies. Let me explain…
Handling Inconsequential Windows Errors: Remove or Ignore?
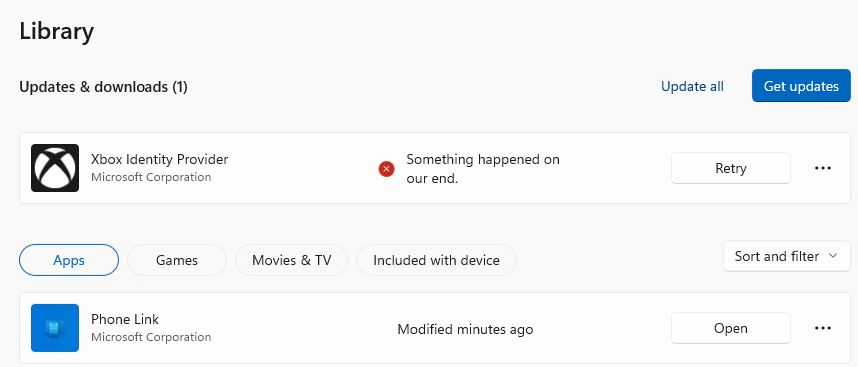
I repeat: I don’t use an Xbox, so I don’t call on the associated complex of Store apps that offer Xbox connections, controls and capabilities. Interestingly, the Store Library shows only Xbox Game Bar. But if you search Apps on the Store Home page, you’ll find dozens of qualifying hits. Interestingly Xbox Identity Provider isn’t among them.
With a little research, I found a website named “Best Gaming Tips” that directly addresses my issue: Xbox Identity Provider Not Working. It includes a helpful PowerShell command sequence to nix this stubbornly uncooperative beast:
Get-appxpackage Microsoft.XboxIdentityProvider | Remove-AppxPackage
It now seems to be gone, too. If I use winget to search for that package name, it finds nothing. And yet, the entry still shows up in Store. I’m restarting and will try again after that… And indeed, that took care of things. Looks like if you change the underlying app structure (or the packages in which they live) you need to stop/restart the Store to let it continue to reflect current reality correctly. Go figure!
For the nonce, the problem is gone. Should I ever have need of the Xbox Identity Provider, I’ll figure out how to re-install it. That’s a bridge to burn some other day. Here in Windows-World, there are always plenty of such opportunities.