Hmmmm. Just saw a fascinating story at Neowin.net. It provides links to some low-cost deals for hard disk drives (HDDs) that range in size from 3 to 14 TB, with prices from US$60 (3TB) to US$210 (14 TB). I’m not endorsing the brand (WD) or the deals (listed from Amazon and — in some instances — Newegg). But I am amazed at just how cheap conventional hard disks can be today. And because HDDs still have their uses — particularly for archiving and spare backups — buying may make sense.
Economics Also Verify That HDDs Still Have Their Uses
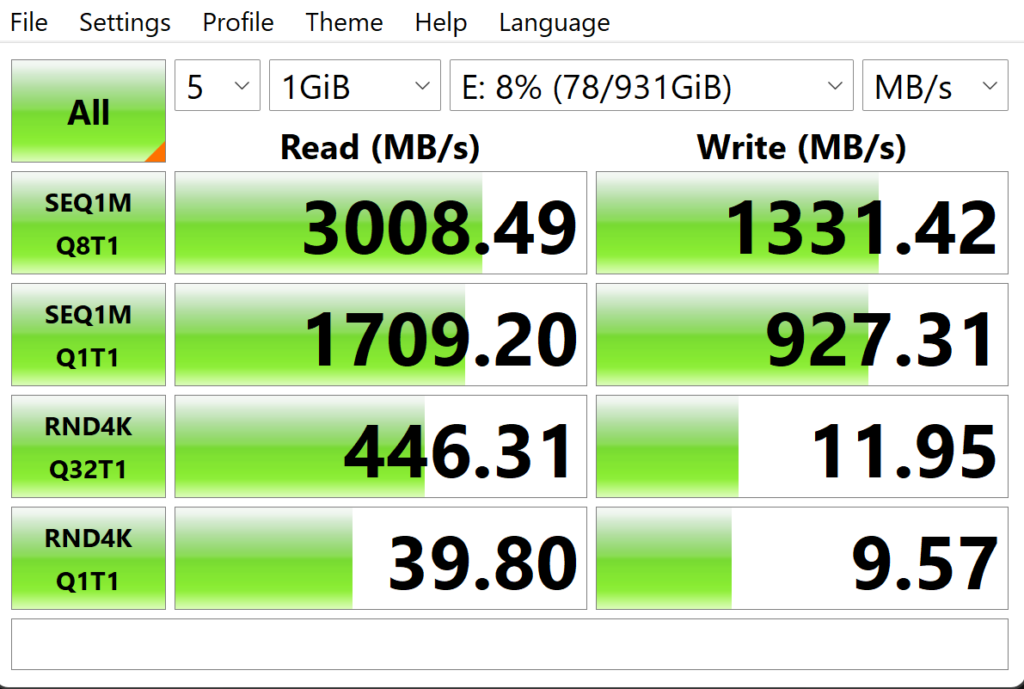
I’m struck by the contrast between HDD and NVMe prices, especially for 4 and 8 TB devices. Looking at Amazon, I see that 4TB NVMe drives go for US$460 and up, with most top-end devices just below or over US$600. When you can find them (not easy), 8TB devices cost from just under US$1,200 to around US$1,500 or so.
The comparison to HDD is pretty stark. The Neowin story cites prices of US$70 for 4, and US$130 for 8 TB. Do the math to figure out the ratios. The 4TB NVMes cost between 6.57 and 8.57 times as much as their HDD counterparts. 8TB models run between 9.23 and 11.53 times as much.
Of course, denser solid-state devices are much more expensive to make. Though higher-capacity HDDs have more platters, achieving denser storage doesn’t magnify costs anywhere near as much. In fact, the HDD cost increment for going from 8TB to 10TB is US$30, and from 8TB to 14TB US$80. That clearly shows the incremental cost of storage is much, much cheaper for HDDs than SSDs.
But given the mind-blowing costs for higher capacity NVMe devices, they’re not going to replace HDDs completely any time soon. They simply cost too much to justify wholesale switchovers. Nobody’s going to use HDDs for serious, real-time workloads any more. They have no place as system drives, either. But for other applications where high capacity trumps I/O performance, they still have a vital role to play. And that explains why I still have over 40TB of spinning storage myself, much of it idle as “backups for my backups.”