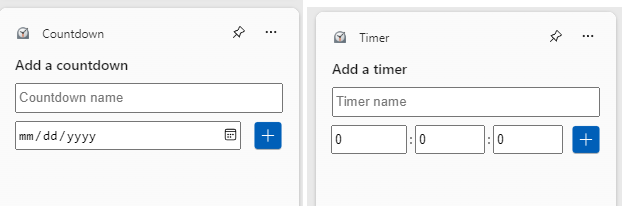
With the arrival of Build 27695, Windows 11 Canary gets new Clock-based widgets. One is named Countdown, the other Timer, so their clock affiliation should be obvious. One or both may be pinned quite easily into the Widgets column at the left-hand edge of the pop-up Widgets panel. Hint: Launch this by entering WinKey+W at some keyboard.
When Canary Gets New Clock-based Widgets, Then What?
You can see what these simple-seeming widgets look like by default in the lead-in graphic (Countdown left, Timer right). Inside the Widget Panel, you must click the top-line “+” (Plus sign) to open the Add a widget display. Then, you can pin either or both widgets, and they’ll start showing up in the Widgets Panel.
It’s always nice when MS starts adding functionality to its facilities. For a long time, that collection was pretty limited. Right now the count is up to 14: Counddown, Dev Home, Family Safety, Focus session, GitHub, Instant Play, Phone Link, Photos, Sports, Timer, Tips, Traffic, Watchlist, and Weather.
And if you click the “Find more widgets” option at the end of the Pin widgets list, you’ll be wafted off to an MS Store page named “Find your next widget.” Highly recommended: it offers better — and more nicely organized — widget listings than a simple search inside Store on “Widgets” offers.
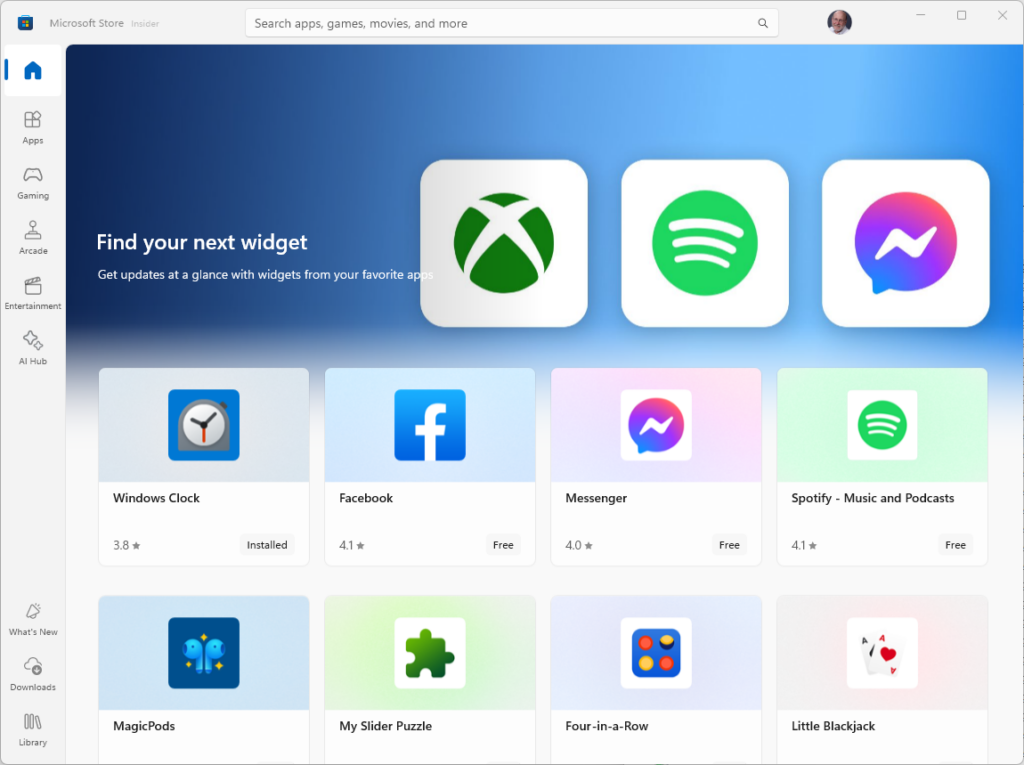 Good stuff: too bad I can’t figure out a URL for that access. You’ll just have to follow the button inside the Widget panel as I did to get there. Enjoy!
Good stuff: too bad I can’t figure out a URL for that access. You’ll just have to follow the button inside the Widget panel as I did to get there. Enjoy!
AFD until Tuesday, September 24
Later today, I’m going in for cataract surgery on my left eye. If all goes well — and they tell me this routine procedure has a 95-99% success rate — I’ll be back at the keyboard next Tuesday. Wish me luck!
BTW, AFD means “Away from My Desk.” I’m not sure if it’s a legit acronym, but I used it to shorten that heading length. Hopefully, it at least makes sense. Happy trails…