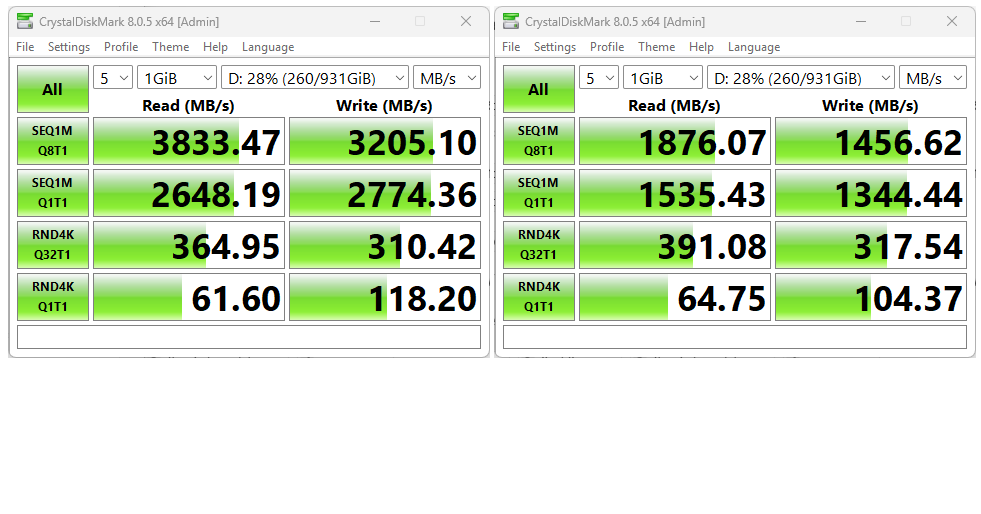
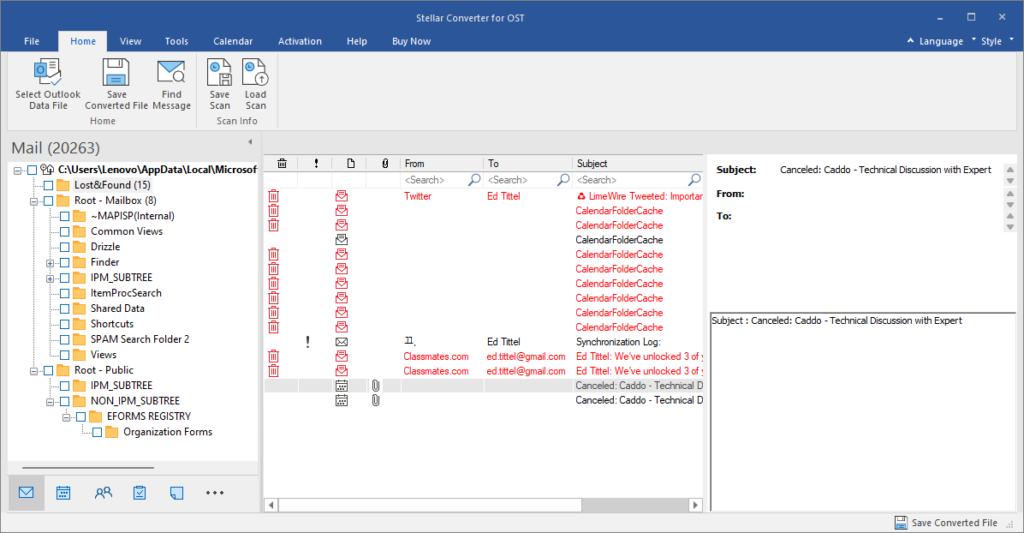
My rationale for keeping the terrific Lenovo Yoga Pro 9i for a couple of extra weeks comes from a recently acquired Maiwo 40 Gbps USB4 NVMe enclosure. Handily, the 9i has two USB-C ports side-by-side. One is rated 40 Gbps, the other 20 Gbps. The lead-in graphic has me comparing USB4 40 vs 20 Gbps via CrystalDiskMark. As you can see, the port speed makes a difference, especially for large block transfers (upper half of each chart).
Comparing USB4 40 vs 20 Gbps: What’s the Diff?
As you can see in the lead-in graphic, the 40Gbps port is faster than its 20Gbps counterpart in 3 out of 4 rows in CrystalDiskMark. It’s double or better for the top 2 rows which involve large (1MB) block transfers. It’s also faster on random writes of 4K blocks, and slightly slower in random reads of such blocks.
Copilot explains these differences as follows (and I am convinced it’s correct because of fundamental principles involved):
- Large reads and writes benefit more from the higher speed . . . because they involve continuous data transfer.
- Smaller reads and writes may not fully utilize the increased speed, resulting in smaller differences.
Indeed it makes sense to me that the 4K transfers (which means such reads involve 8 512-byte sectors per read or write) would be less sensitive to bandwidth than 1 MB transfers (2,048 512-byte sectors per read or write, as in 211 transfers overall for each such operation). There’s a lot more time for the speed difference to manifest for those larger transfers. The smaller ones are so fast, the channel speed differences don’t matter much (or at all).
Comparing Backup Times
But CrystalDiskMark is a synthetic benchmark, so it’s not entirely clear how accurately it reflects speeds when performing various operations. For me, the ultimate test of an external USB storage device is how fast it can complete an image backup of the PC’s boot/system drive. Indeed backup and restore top my list of “things to use external USB storage for.” So let’s compare those numbers, shall we?
Because my fave backup tool — namely, Macrium Reflect — is no longer free, I installed and used EaseUS ToDo Backup Free instead. I ran two complete backups with the same drive, same cable: one thru the 40Gbps port, the other thru the 20 Gbps port. File Explorer reports the size of the C: partition at 73GB; other partitions on that drive weigh in at over 1GB total (interestingly, EaseUS reports backup size at 119.5GB). I used 120GB as my backup size in the following table. I also checked Settings | Bluetooth & devices | USB | USB4 hubs and devices to confirm that the first timing used the 40Gbps and the second the 20Gbps USB-C ports.
Port Total Time GB/min 40Gbps 03:22 (202) 35.64 20Gbps 05:11 (311) 23.15
As you might expect the difference is not linear. The 40Gbps backup averages about 35% faster, not 100% as a purely linear ratio would dictate. Even so, this saves 109 seconds (01:49) on backup time. As the backups get bigger, the gap widens. Very interesting!
More for Less
Right now a 40Gbps NVMe enclosure (with cooling fan) costs (US$70) about fifty bucks LESS than what I paid for a 20Gbps device two years ago (sans fan). Thus, I’d say the difference was definitely worth it.
If you’re buying new, there’s no reason to consider an older 20Gbps device. The real question for those with PCs or laptops 2 years old or older is: does this speed difference justify buying a newer computer? Only you can decide for yourself. For me, it’s pretty compelling . . . but for now, I’m using a loaner unit from Lenovo to measure this capability. I haven’t shelled out to buy a brand-new machine with my own cash recently, either. But I’m thinking about it, hard.