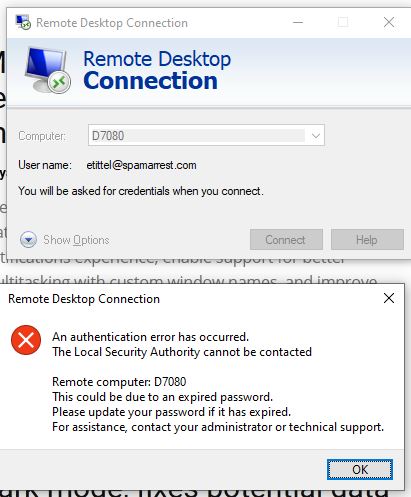
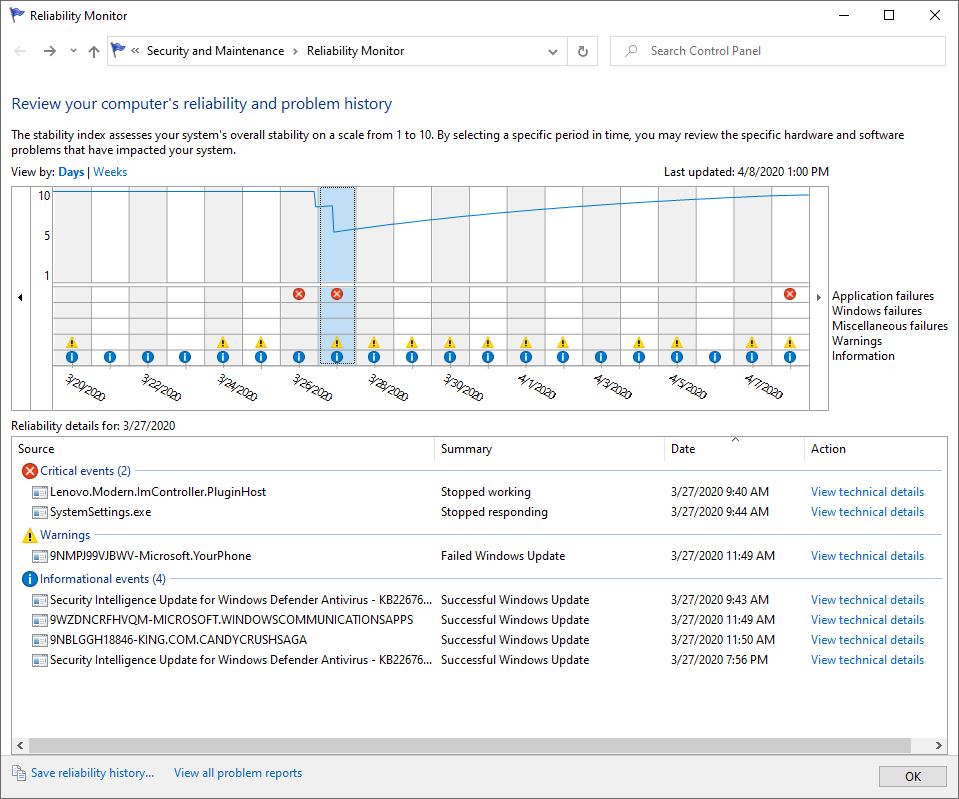
I’ve been raving about the SFF Dell Optiplex 7080 Micro a fair amount lately. I remain convinced it’s a good purchase and will be a great machine for long-term use. That said, there is the proverbial “one thing” that lets me know for all its glories, it’s still a Windows PC. I’ve been dealing with an RDP mystery — as shown in the lead-in graphic for this story — that actually affects RDP traffic in both directions. Its 20H2 RDP mystery remains unsolved, as all my troubleshooting efforts so far have failed.
Read on, though: I did eventually figure this out, and get RDP working. It turned out to be a basic and obvious oversight on my part. Sigh.
What Do You Mean: 20H2 RDP Mystery Remains Unsolved?
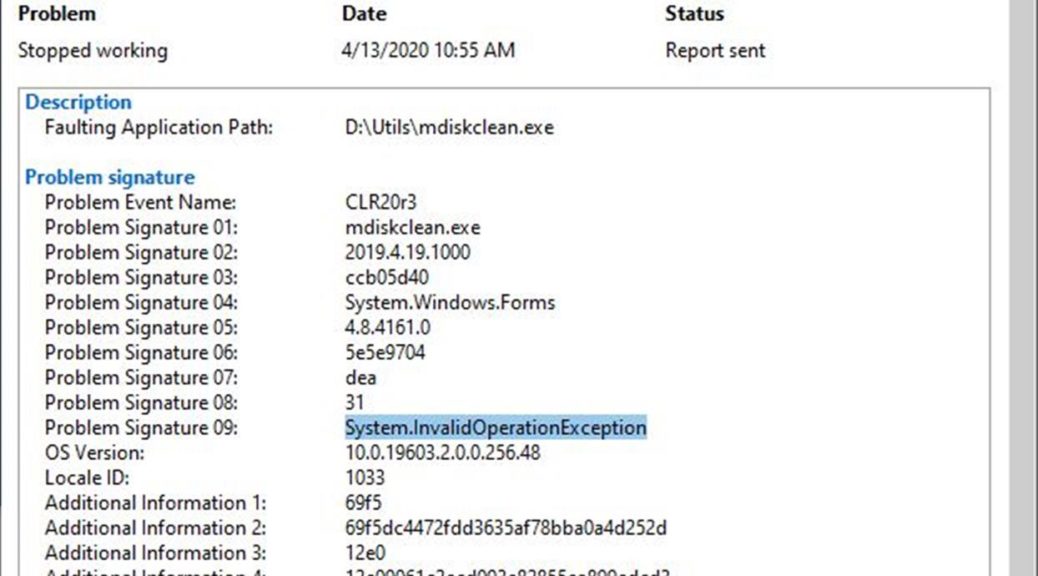
Despite chasing down a large laundry list of things to check and set, I get password related errors when trying to RDP into or out of the 7080 micro. The lead-in graphic shows what happens when I try to RDP into the box. When I try to RDP out of the box, I get an out-and-out invalid password (“may be expired” error) instead.
Obviously, something funky is up with authentication on this Win10 install, because when I try to access the device through the File Explorer network connection, I get a request for network credentials, too. Again, presenting valid credentials doesn’t work. I see a “not accessible” error message instead:
 Here’s the list of what I’ve tried so far:
Here’s the list of what I’ve tried so far:
- Double-checked Remote Access is enabled.
- Relaxed all relevant settings in Advanced Network Sharing for Private, Guest/Public, and All Networks categories.
- Enabled all Remote Access checkboxes in Defender Firewall settings.
- Ran the Network Troubleshooter
- Ran the Microsoft Support and Recovery Assistant
It’s the Account, Stupid!
After noodling about with this for a couple of hours I realized that I had defined a local acount as admin. Worse yet, I had not promoted my Microsoft Account on the Optiplex 7080 Micro from ordinary user to administrator.
Because I was using my MS account credentials to attempt network login and access, I didn’t have permission to do the password lookups in LSASS needed to make the process work. Once I promoted that account to admin level, everything started working.
Sheesh! Talk about an obvious mistake. As with many problems with Windows 10, this one turns out to be entirely self-inflicted. At least, I know who to blame!