Thanks to a recent story in Windows Latest, I just learned that a new version of the Chinese-built MS store app named PC Manager is out. For those who don’t already know, this tool offers performance boost, health check, storage and startup cleanup tools, and more. Though I’ve heard from plenty of used inclined to be skeptical, if not distrustful, of this tool, I’ve never had it cause me a problem in the 16 months I’ve been writing about it (here’s my first intro post from July 2023). With the latest 3.14.10.0 release, PC Manager gains advanced browser cleanup tools.
Showing PC Manager Gains Advanced Browser Cleanup
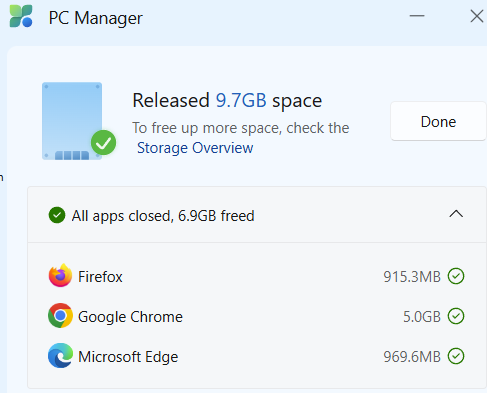
You can see the results of such a cleanup in the lead-in graphic: especially for Chrome, they’re substantial (5.0 GB). Of the 9.7 GB in disk space that the Deep Cleanup tool freed up, 6.84 GB (~70%) comes from this newly-minted browser cleanup facility. IMO, that’s pretty major — especially because web browsers account for plenty of the CPU and memory cycles, and disk and memory space on Windows PCs.
Indeed, Copilot says that on a typical Windows PC, web browsers generally consume around 10-20% of the total runtime resources (CPU, memory, network and storage). I think that’s on the low side, but then I nearly always have 20 or more Chrome, Edge and Firefox processes visible in Task Manager (each), and at least a half-dozen tabs open in all 3 browsers. Seems like double (or more) in my case as compared to Copilot’s estimate.
Whatever your typical usage patterns might be, this newly-added cleanup tool will probably be worth running once in a while. I’m going to try it daily and see if it makes any difference.
Give It a Try?
If you’re not using PC Manager already, this new facility makes it even more compelling. If you don’t have it installed, you can find in the MS Store, or grab it via this MS Store link. Go ahead, check it out. You may enjoy it!