With each Patch Tuesday, MS releases a new version of the Malicious Software Removal Tool (MSRT). Just yesterday, I learned about a similar but different tool named Microsoft Safety Scanner (MSERT.exe). At first, I did a double-take to make sure it wasn’t a typo. It’s not, as the Safety Scanner Docs page attests. (Here are live links to the 32-bit and 64-bit downloads mentioned in the lead-in graphic.) Here, I’ll explore what’s involved in using Microsoft Safety Scanner, aka MSERT.exe.
Explanation Precedes Using Microsoft Safety Scanner
MS explains the tool thusly “a scan tool designed to find and remove malware from Windows computers.” It goes on to says “Simply download it and run a scan to find malware and try to reverse changes made by identified threats.” Like the MSRT, the MS Safety Scanner gets updates and new signatures all the time, so MS recommends that you always download a fresh copy any time you’d like to use it. They also observe that it’s only worth using for 10 days, after which one MUST download a new version.
Here’s how MS describes the MSRT on its download page:
Windows Malicious Software Removal Tool (MSRT) helps keep Windows computers free from prevalent malware. MSRT finds and removes threats and reverses the changes made by these threats. MSRT is generally released monthly as part of Windows Update or as a standalone tool available here for download.
I’ll be darned if I can tell much difference between them. Nor do I see much distinction in third-party coverage. That said, Explorer sees big differences in size between the two, to wit:
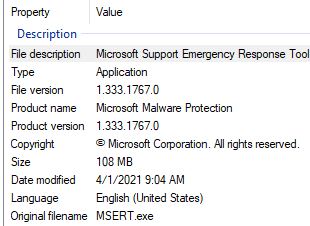
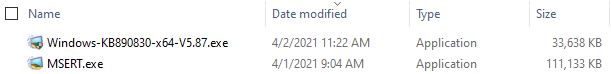 Notice that MSERT.exe shows up as itself, while MSRT shows up as KB890830, version 5.87. Because MSRT is released monthly through WU, it apparently keeps the same KB number, but gets a new version number with each release. MSERT is not so readily obliging but does show that information on its Properties/Details page. That’s where I learned that MSERT stands for “Microsoft Support Emergency Response Tool.”
Notice that MSERT.exe shows up as itself, while MSRT shows up as KB890830, version 5.87. Because MSRT is released monthly through WU, it apparently keeps the same KB number, but gets a new version number with each release. MSERT is not so readily obliging but does show that information on its Properties/Details page. That’s where I learned that MSERT stands for “Microsoft Support Emergency Response Tool.”
Full name plus file version info readily available here.
[Click image for full-sized view.]
Let’s just say this is another tool from MS you can run at your own discretion to check a Windows PC for malware, and attempt cleanup. All this makes me curious to understand why we have access to not one, but two, such tools. Even the best of third-party explanations/explorations tend to be a bit shaky, like this Tom’s Hardware Forums item. Even my home forums community at TenForums is pretty much mum on differences, to my consternation and regret.
Using Microsoft Safety Scanner
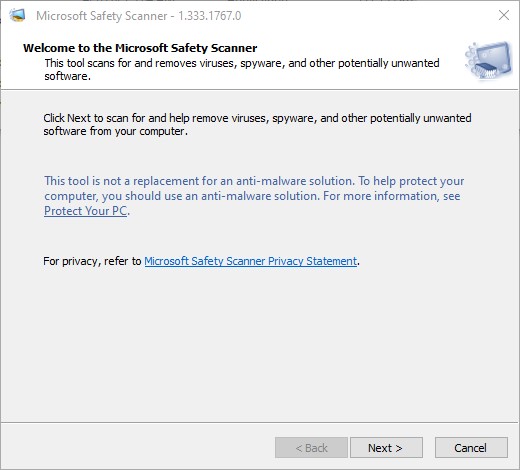
The .exe file is portable and runs from anywhere (including the Downloads folder). The Docs don’t say one should run the program as administrator, but I did so anyway. It presents a EULA to which you must agree before it does its thing. Next you get a welcome/disclosure screen:
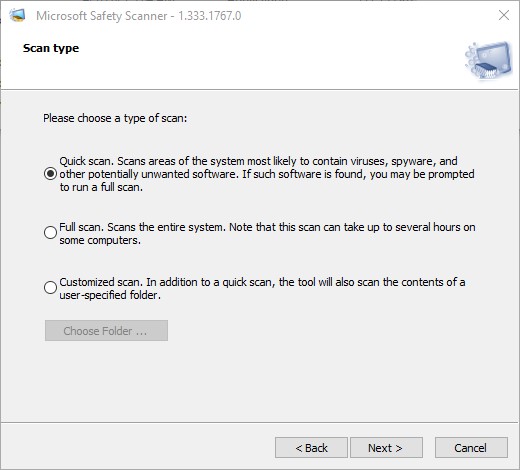
Click Next, and you get your choice of scan types (quick, full, or customized).
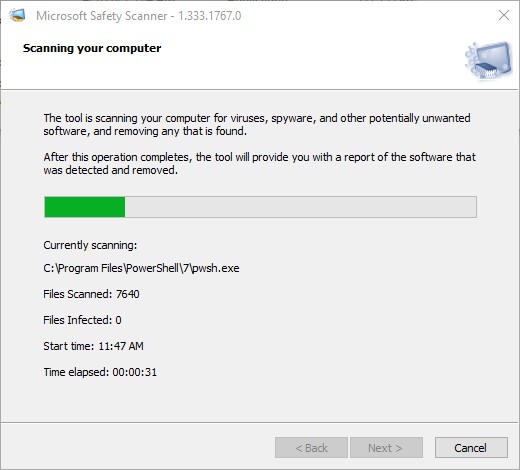
Then, it scans your “most likely compromised” files under quick scan.
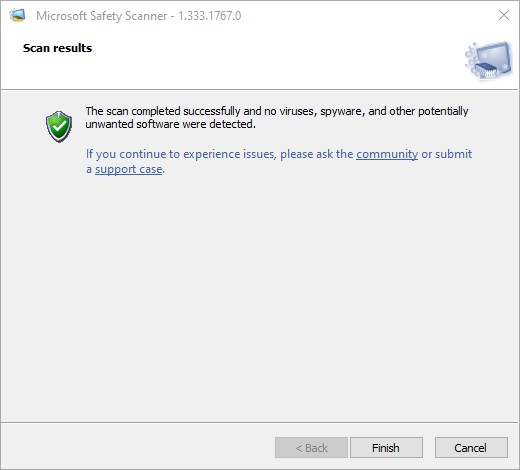
On my production PC, the whole process took about 3:00 and produced the following results.
Nothing to see here folks, please move along. A clean bill of health, in other words.
Upon completion, the log file (named msert.log) shows nothing informative about cleanup or actions taken (probably because it found nothing to clean up). Here’s a NotePad++ view of its contents (click to view full-sized, as it’s a little hard to read in native WordPress resolution):
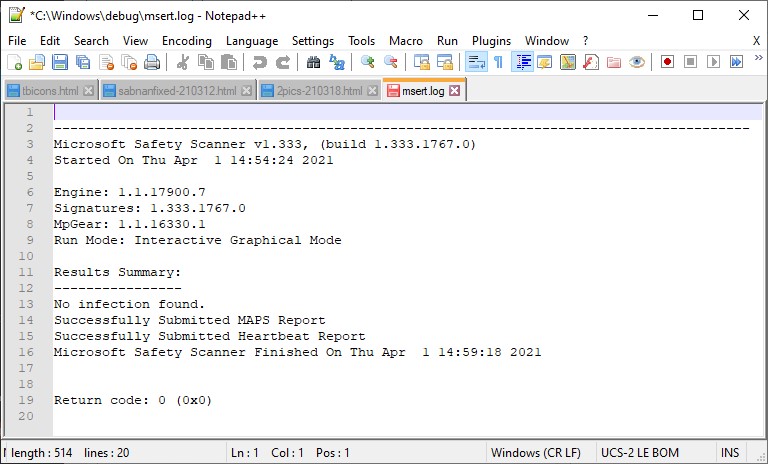 I’m still not sure if you and I really need this tool or not, but it’s nice to know it’s available on demand should you wish to make a malware scan and clean-up pass over your Windows PC. The whole thing still has me wondering…
I’m still not sure if you and I really need this tool or not, but it’s nice to know it’s available on demand should you wish to make a malware scan and clean-up pass over your Windows PC. The whole thing still has me wondering…