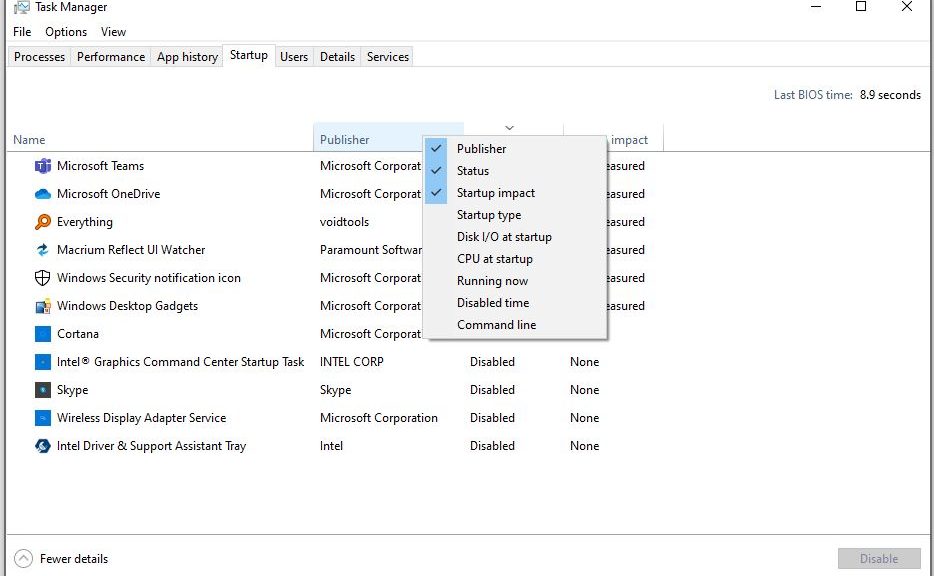
Here’s something new and helpful about working with Task Manager. Take a look at this story’s lead-in graphic. It shows you can right-click any column header in Task Manager’s Startup tab, to see a pick list of columns (checked items). Add the “Startup type” and “Command line” items, and learn more about the startup entries they describe. In fact, they helped me with identifying Windows 10 mystery startup items on my production PC.
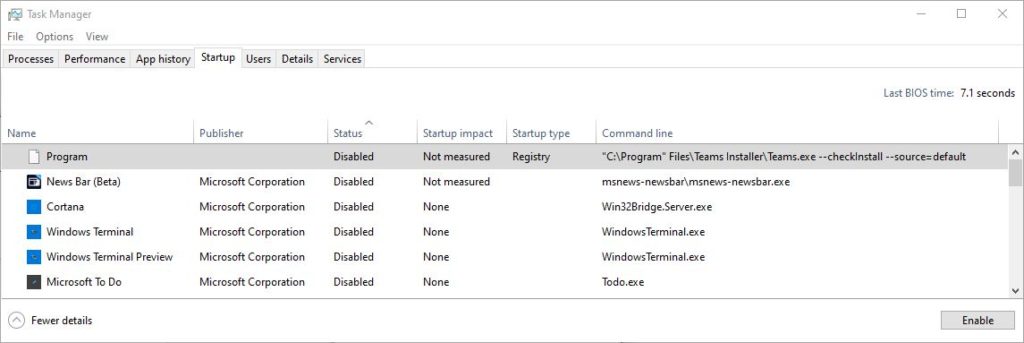
When a generic “Program” entry showed up in Startup items, adding fields let me see where it was coming from.
[Click item for full-sized view: see top table entry.]
How-to: Identifying Windows 10 Mystery Startup Items
The “Startup type” tells you where the directive comes from. For “Program” it came from the Registry. Better still, Command line data tells you what Startup executes as Windows 10 gets up and running. The particular instruction is malformed and can’t work:
"C:\Program" Files\Teams Installer\Teams.exe --checkinstall --source=default
The closing double quote is misplaced (it should be at the end of the line). Also the directory path referenced in the command does not actually exist on the PC in which this Registry entry resides.
What did I do about this spurious startup item? I cheerfully disabled it. Indeed, that means there’s an orphaned key-value pair in my registry. I can live with that. I do intend to report it via the Feedback Hub, because it definitely includes a syntax error (the misplaced closing double quote). Otherwise, though, it’s no big deal and I’m satisfied to disable it.
[NOTE} Here’s a shout-out to WinHelpOnline, whose story What is “Program” in Task Manager Startup Tab helped me understand my mystery item. It’s worth reading in its entirety for those who want to learn further details about what’s going on, and how to remove related orphaned registry items.