Sometimes, it isn’t until things go terribly wrong that one appreciates the power of simple syntax. Check out this TenForums post, which explores the impact of the WinKey+P gone wrong: Win p key pressed. Because WinKey+P powers display projection, a user’s nephew’s wrong menu choice made him think he’d lost access to 2 of his 3 displays in a multi-monitor configuration. Not so!
WinKey+P Powers Display Projection — Usually Into a Menu
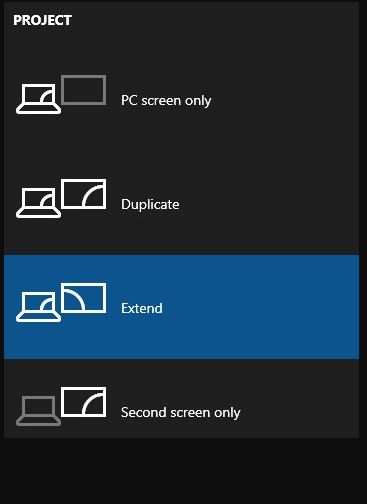
Normally, when you strike Winkey+P on a Windows 10 or 11 PC, you’ll get a pop-up menu like the one shown in the lead-in graphic. It highlights the current setting — Extend in my case, because I have my desktop extended over a pair of Dell 2717 monitors. Overall, it offers these four settings:
- PC Screen only: (tantamount to striking WinKey+P once)
- Duplicate: copies primary monitor to all other monitors (select by striking WinKey+P twice)
- Extend: extend the desktop across all available monitors (select by pressing WinKey+P three times)
- Second screen only: use only Display #2 for graphical output (select by pressing WinKey+P four times)
Our hapless user’s nephew struck WinKey+P once, which apparently forced his PC into “PC Screen only” mode. On my PC, however, I got the menu shown above, and was easily able to move among the selections using my mouse.
When Key Combos Go Wrong, Try More!
Interestingly, advice on TenForums about what to do in this situation is spot on. It reads “Did you try pressing ‘WinKey+P’ again? Sometimes a key acts like an ‘on off’ switch.” In this case, our user wanted to press WinKey+P 3 times to get to the extend option through the keyboard. There’s no discussion of using the menu instead, which I find infinitely preferable.
For some odd reason I’m reminded of one of William Blake’s epigrams from his Proverbs of Heaven and Hell:
The fool who persists in his folly soon becomes wise.
This turns out to be good, if oblique, advice when dealing with unwanted WinKey key combinations. As for myself: I’d have looked it up online, and found all the insight I ever could have wanted, and more.