I’ve been a member over at TenForums for almost 7 years now. In fact, I joined up on November 14, 2014 shortly after the first Technical Preview emerged. This weekend, I was relieved to discover that the batch file Shawn Brink created as a WU reset tool works on Windows 11, too. (The preceding link goes to a tutorial that provides a download and explains how to use it to reset Windows Update, or WU).
It’s a Relief that WU Reset Tool Works on Windows 11
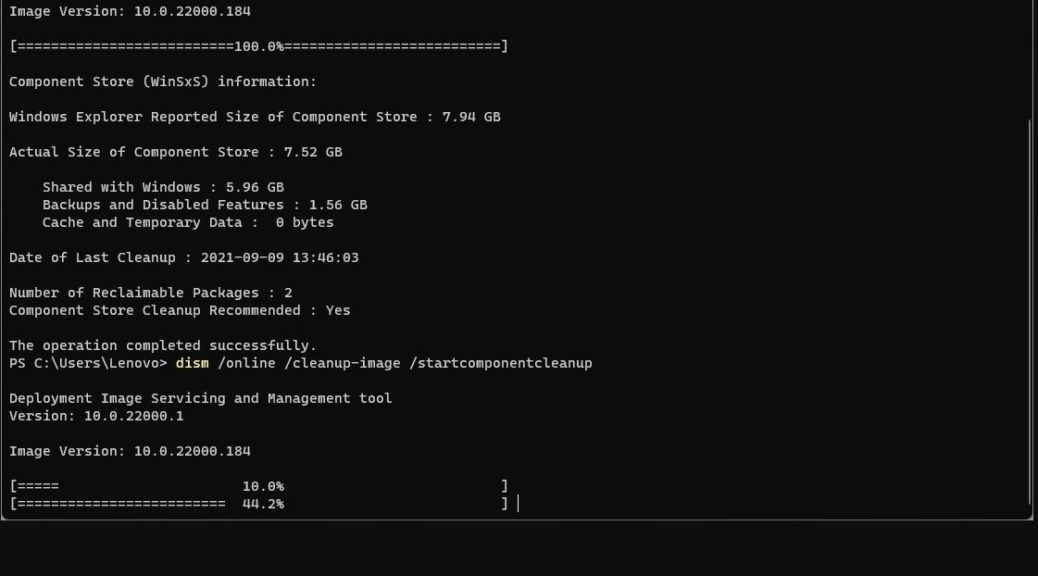
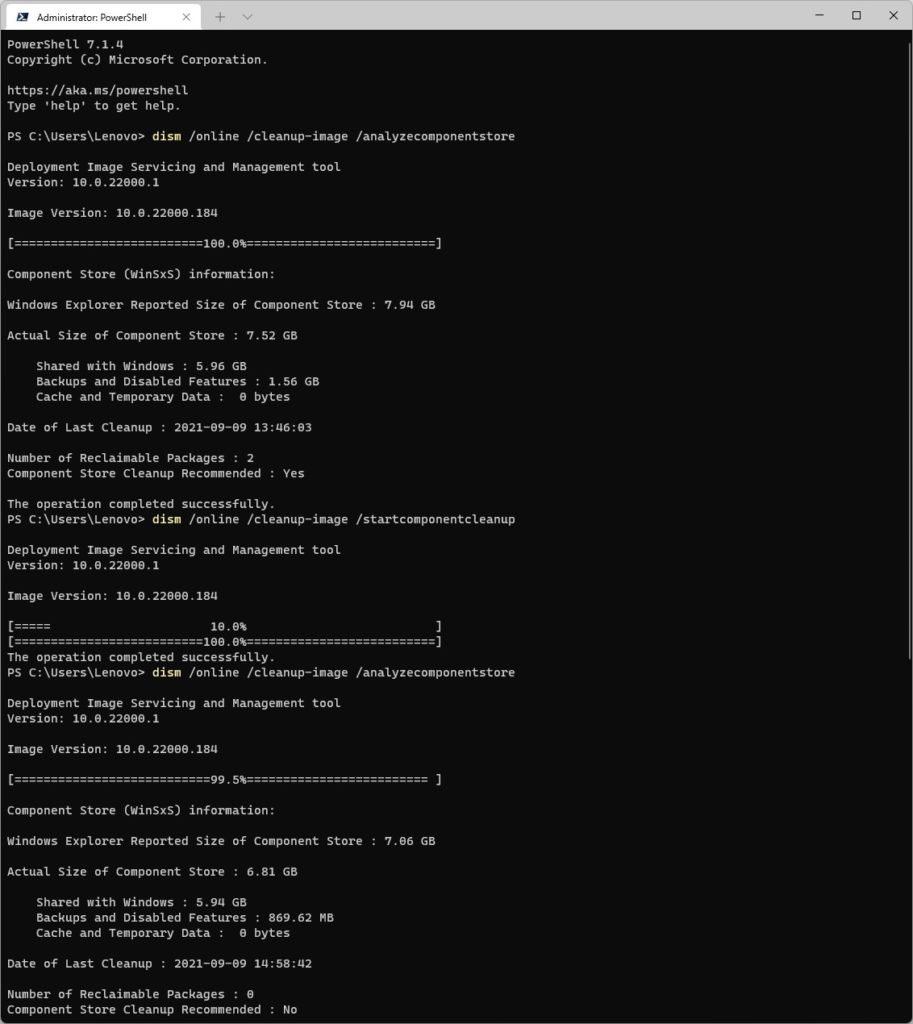
My Lenovo ThinkPad X380 Yoga test machine would start downloading updates from WU just fine. But part-way through the download process, progress would stop. Eventually, I would get an “Update failed…” error message, with a Retry button. After several tries, each with its own similar failure, I knew sterner measure were needed.
I actually keep the batch file from the afore-linked tutorial on my shared desktop in OneDrive. It’s called
Reset_Reregister_Windows_Update_Components.bat
and it does a thorough reset of the Windows Update environment. It begins by halting all update-related services, then it empties all folders where recently-downloaded update files reside, checks (and if necessary resets) various WU-related registry settings, then restarts those same services. A reboot follows next, after which one can try one’s luck with WU again.
So I ran the batch file in an administrative cmd prompt on the affected machine, let it do its thing, then restarted that PC. Presto! After restarting, my next update attempt succeeded. I wasn’t 100% sure it would work on Windows 11 because the tool was built for Windows 10. But to my great delight and relief, it set the Windows Update environment back to working order. And thus, I was able to catch that machine up with the current state of the Dev Channel.
Should you ever find yourself in a similar situation, I recommend the tool and its accompanying tutorial highly. Find it at TenForums as Reset Windows Update in Windows 10. Hopefully, Mr. Brink will soon do a run-through to create a Windows 11 specific version. Should that occur, I will add a link to that version here as well.