I’m always learning something new or surprising about Windows. In this case, I’m talking about Windows 11 since 22H2 came along in September 2022. That’s nearly 3 years ago, so to discover something mostly missing in new-ish (and brand-new) eval PCs from OEMs such as Lenovo, dynabook, and Panasonic is my surprise of the day. I’m talking about a feature in Windows Security — namely Windows 11 Smart App Control — about which I’ve been mostly oblivious until today.
This morning, I re-read a piece from Paul Thurrot from last Thursday (June 26) entitled You Use Windows. Be Resilient (it’s Premium content, so you’ll need to sign up for a membership to read this: sorry). Under the heading of app protection, it off-handedly mentioned Smart App Control as follows:
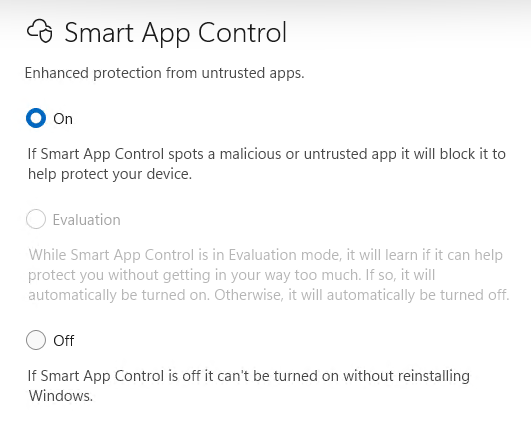
Windows 11 has a feature called Smart App Control that’s in a weird state of flux and may or may not be configurable on your PC. Open Windows Security and navigate to App & browser control > Smart App Control, and see whether you can enable it. If you can, do so.
“Hmmm” I thought to myself, I don’t recognize this. “I’ll go look.” On the vast majority of new machines (all issued in 2023 or later) I found that — as you can see in the lead-in graphic– Smart App Control was turned off. And right below that status: a can of interesting worms. Gotcha!
A Gotcha in Windows 11 Smart App Control
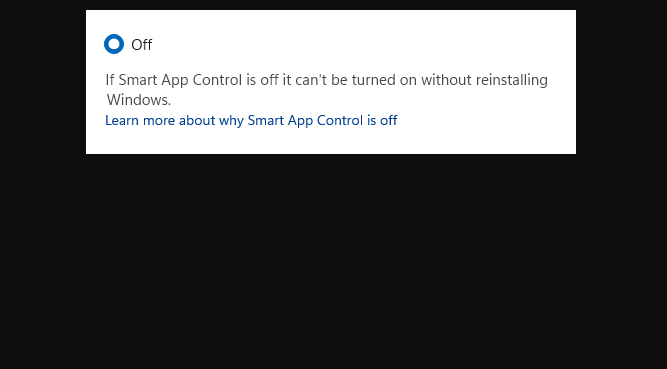
That can of worms is, of course, the explanation beneath the “Off” toggle that reads “If Smart App Control is off it can’t be turned on without reinstalling Windows.” Really?!?!
That’s right. Apparently, enough people have noticed this distressing detail that MS has put together a FAQ around this very topic. It’s the one that’s accessible from the link at the bottom of the lead graphic that says Learn more about why Smart App Control is off.
TLDR: Smart App Control hooks into the OS at a deep enough level that if it’s not there when the OS gets laid down, a new, clean install is necessary to put it there from inception to make sure it works like it should. In other words, if your install of Windows 11 predates 22H2 — as so many of mine do — or the OEM doesn’t enable this feature as part of their initial Windows 11 image install — you can’t have it without an OS do-over.
What’s in My Field of (New/ish) View?
With this item in mind I examined all of my newest PCs, only to find that just one of them supports Smart App Control (SAC), albeit in “Eval mode.” Here’s what that looks like:
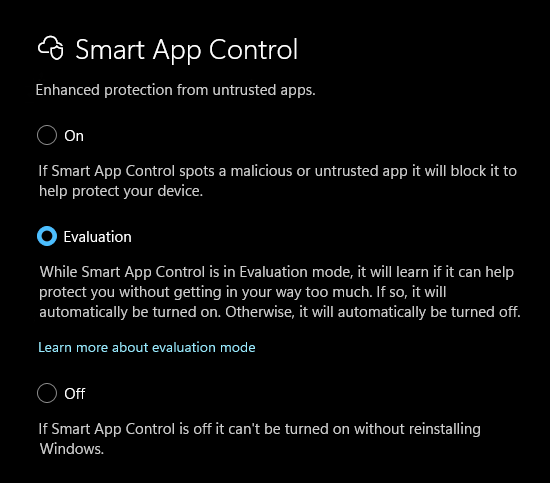
Of all my relatively new PCs only the dynabook X40M2 supports SAC (in evaluation mode).
Here’s a list of those PCs, for the record:
- The preceding graphic shows I’ve got it in “Evaluation” mode on the dynabook X40M2 laptop I received earlier this month.
- It’s turned off on the Lenovo ThinkPad T14s (original Windows 11 install date November 2024)
- It’s turned off on the Lenovo ThinkStation P3 Ultra (original Windows 11 install date November 2023)
I just got an eval from Lenovo for its new Copilot+ capable AIO (Model Lenovo Yoga AIO 9i last Friday. I haven’t unboxed it yet, so I can’ t yet say if it has it turned off or not. I’ll report back later.
Small Sample Size Warning & Wondering
The sample size is ludicrously small (3 machines so far, with a fourth on the way later this week). But it’s now a bit clearer to me why I haven’t run into Smart App Control before. It’s just not that widely dispersed in the field yet. And I bet a lot of other long-time Windows Pros like me don’t know they can’t have it on older PCs unless they bring it in via a clean Windows 11 install.
Very interesting! Let’s just hope the dynabook survives Evaluation mode with Smart App Control intact, so I can learn more about how it works, and what it really does. And isn’t that just the way things often work, here in Windows-World? You betcha!