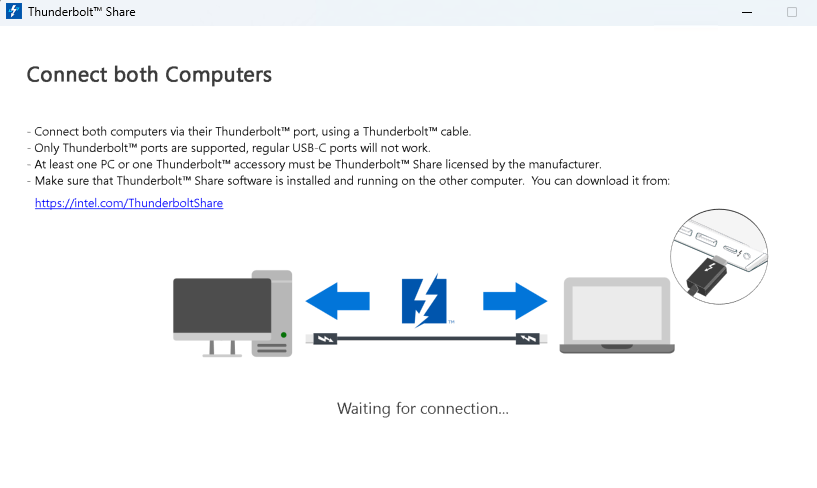
OK, then. I asked Lenovo to send me another Thunderbolt 4 capable laptop so I could try out the new Intel Thunderbolt Share app. Looks like I’m at least temporarily stymied, and have learned some things I don’t especially like, either. Indeed, Thunderbolt Share gets interesting from the get-go possibly because of licensing issues. Right now, I’m stymied because when I run a TB4 cable between my 2 TB-equipped laptops right now, I can never get past the “Waiting for connection” screen shown above. Sigh.
Thunderbolt Share Gets Interesting Because…?
Notice the disclaimers beneath “Connect both Computers” in the foregoing screencap. I may be stuck on the clause that reads:
At least one PC or Thunderbolt accessory must be Thunderbolt Share licensed by the manufacturer
From what I can tell, the newest of my pair of PCs — the only one that could possibly qualify here — had its Windows image burned on November 20, 2024. Given that Thunderbolt Share made its debut in May of the same year, it’s entirely possible that Lenovo didn’t license this program for the ThinkPad T14s Gen5. At any rate it’s not working between my only TB4-capable laptops right now. I’ve asked Lenovo for help, and we’ll see what happens. But there’s more…
Thunderbolt Share Won’t Open in RDP Session
My usual way of working on test and eval PCs is to RDP using Remote Desktop Connection (mstsc.exe) on my primary desktop. That’s what I tried first to get into Thunderbolt Share on the two target machines. Guess what? Thunderbolt Share won’t launch from inside an RDP session. I have to physically use the target PCs to get the app to run. I have to laugh…
Once launched, it keeps running if I then remote into either the P16 or the T14s. But of course, it’s stuck at “Waiting for connection” right now. So I’m getting nowhere, fast. That means my plans to compare TB4 cable transfer speeds against GbE and Wi-Fi transfers are on hold for now. Stay tuned. I hope to get this straightened out soon.