Sometimes, you just get lucky. This Monday, I saw Rich Woods’ review of the Lenovo X1 Nano laptop at NeoWin.net. Immediately thereafter, I emailed my contact at Lenovo to ask for a review unit. Yesterday (one day later) I had that unit in my hands. That’s lucky! This mini-review is my X1 Nano first look report. Also, I’ll be writing about this light, compact, and powerful unit one or two more times in the next couple of weeks. Then, alas, I must return it.
Impressions from X1 Nano First Look
I’m a fan of the more compact X series ThinkPad laptops. I currently own an X220 Tablet (2012 vintage), 2 X380 Yogas (2018) and an X390 Yoga (2019). I like the portability of the 13″ form factor. I like the ease with which I can throw a unit (or two) into a carrying sleeve, a briefcase, or a backpack. On family trips especially, I’m used to taking two small laptops along. Thus, I can still keep up with email and post blogs while on the road. And my wife and son can use the other laptop when their smartphones aren’t enough.
I came into this review thinking the Nano would be a great candidate for family laptop on the road. I came out of it thinking that it would make an excellent (if lighter duty) candidate for work laptop on the road. I’ll need more time with the unit to suss this out further.
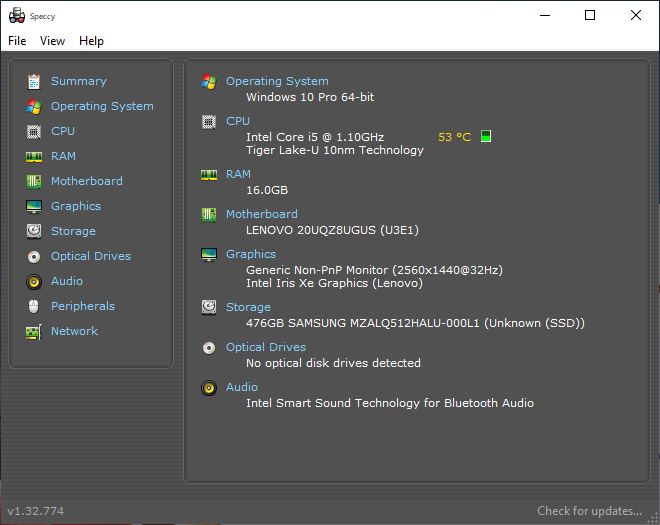
PiriForm’s free Speccy tool shows the basic components in this review unit.
X1 Nano Review Unit Speeds & Feeds
OK then, it’s got a Tiger Lake (11th generation) i5-1130G7 CPU, which runs at 1.10GHz on four cores and eight threads. Burst mode goes to 1.80 GHz for single-threaded tasks. It also comes with 16 GB of surprisingly fast LPDDR4-4266 RAM. It’s the first laptop I’ve used with Intel Iris Xe graphics. (Once again: these are surprisingly fast and also capable.)
There’s a Samsung OEM 512 GB SSD (NVMe PCIe 3.0 x4) that’s reasonably fast (NotebookCheck calls it “entry-level to mid-tier by H1 2020;” one year on, it’s pretty much straight-out entry level). It’s got a non-touch, 2560×1440 (2K), 450 nits, 16:10, sRGB display that’s crisp and readable at default resolution. The only ports on the device are two Thunderbolt 4 USB-C connections: one labeled for power-only, the other labeled for power and data.
It also sports a speedy Intel AX201 Wi-Fi chipset that meshed quite nicely with my Asus 802.11AX router. (Access speeds of 400 Mbps and better, in a busy, signal-rich office environment.) Oh, and it has a fingerprint reader and a 720p Windows Hello capable integrated Webcam, too.
What’s missing on this unit for those who don’t have a Thunderbolt dock handy? (I have several.) At least one USB 3.0 Type A port, and a micro SD port for added, onboard flash storage. With even high-capacity uSDXC cards now pretty affordable, I do indeed wish Lenovo had found a way to squeeze one in somewhere.
What Makes the X1 Nano a Standout?
It weighs only 906 grams (1.99 lbs). It’s got a carbon fiber top deck and a (nicely coated) magnesium bottom deck. The keyboard is about 10% smaller than the one on my other X model ThinkPads. Even so, it feels (and works) so much like those others that I can’t tell any difference. And for somebody like me who makes his living by typing on a keyboard, that’s a big thing.
The display is also pleasingly bright and clear, and the Iris Xe graphics are fast, crisp and powerful. I’m no gamer, but I couldn’t make the display choke up even by throwing graphics pop-ups at it. Working with my usual mix of multiple Chrome, Firefox and Edge windows, plus MS Word for writing, I was impressed. It works and feels just like my now-aging but still capable i7-6700 Z170 desktop (32 GB RAM, Samsung 950 Pro SSD, GTX 1070) on my typical in-office workloads. Even comparing CrystalDiskMark 8.0.1 results for the two primary drives, they’re almost identical.
More to Come in Days Ahead
Right now, my response to this PC is an enthusiastic “So far, so good.” As equipped, this unit’s MSRP on its Lenovo product page is US$1727.40. That makes it about $100 less than a 10th generation, i7-equipped, non Iris XE (Intel 620 UHD) touchscreen ThinkPad X1 Yoga Gen 5.
Were I myself to buy one of these, I would spring the extra $120 for an i7 CPU. It uses an M.2 2242 NVMe drive, of which 1 TB units are not yet readily available on the aftermarket. Thus, I would probably buy the 256 or 512 GB SSD and then do a swap myself, when higher-capacity, higher-performance options go up for sale.
Other than that, it’s a delightful little laptop. I recommend it highly, subject only to my reservations. Those are: few ports, no SDXC slot, and a mildly painful ouch factor on price. But that’s how it is for “thin-and-light” laptops, isn’t it?