I’ll confess. I’ve been a fan of lostindark’s DriverStore Explorer tool for a decade or more now. Aka RAPR.exe, this tool lays bare the complete contents of the Windows DriverStore for versions 7 and newer. It also makes it pretty easy to clean up old drivers, thanks to its “Select Old Driver(s)” (SOD) button. That what makes my main Windows 10 driver go-to tool DriverStore Explorer. Accept no substitutes!
Windows 10 Driver Go-To Tool DriverStore Explorer Shows ALL Drivers
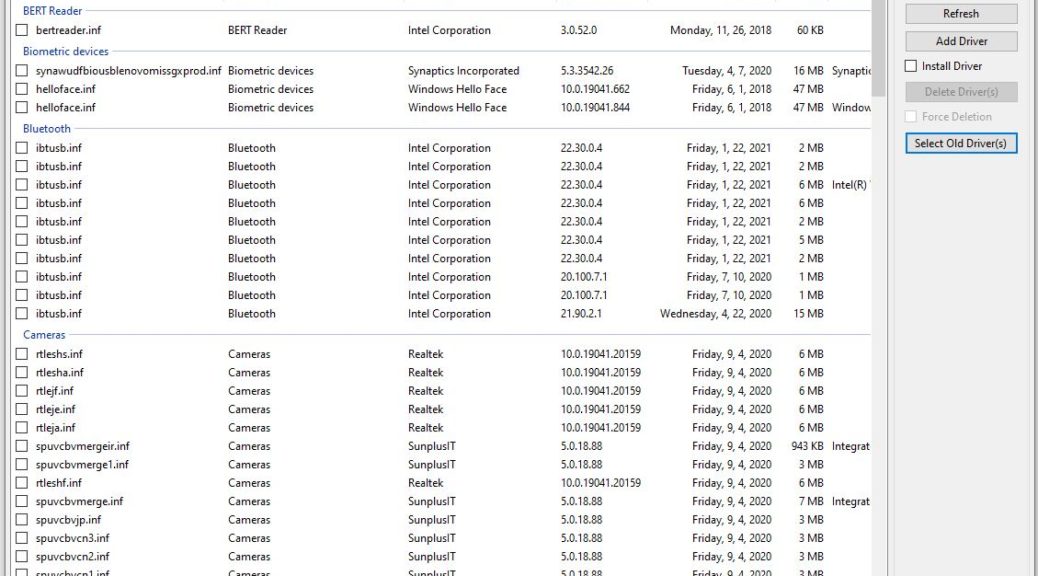
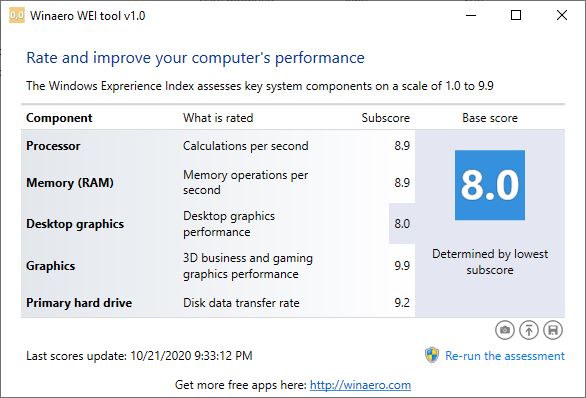
If you look at the lead-in graphic for this story, you’ll see 8 copies of the same Intel Bluetooth driver installed on my Lenovo X1 Extreme (Gen 8) laptop. Three older versions of the same driver are also present. When I click the SOD button, 6 copies of the 1/22/2021 driver get marked, along with all 3 2020 versions. When I then click the “Delete Driver(s)” button, and confirm that instruction, exactly 2 copies remain behind. Because they’re different sizes — one is 2 MB, the other 6 MB — I conclude they’re different even though they share a common filename. All the rest of them (31 MB total) are gone.
Some Drivers Are Special Cases
Sometimes, when you use the SOD button, a selected driver won’t be deleted. Typically, that means the still-present item is in use, despite being older than something else also present in the DriverStore. You can force deletion on such items, but are risking system instability by doing so. I recommend against this unless you’re dead sure the newer driver will work correctly.
Even so, I typically recover anywhere from 50MB to several GB of disk space when I use RAPR to clean out my Windows 10 DriverStores. Nvidia graphics drivers are particularly big space consumers (and generally run from 900 MB to 1.1 or 1.2 GB in size). Cleaning up a half-dozen of these can recover some real space.
Try it for yourself. You can’t help but like it. Visit the GitHub page for more information and the most current download. As I write this story, that version is numbered v0.11.64.