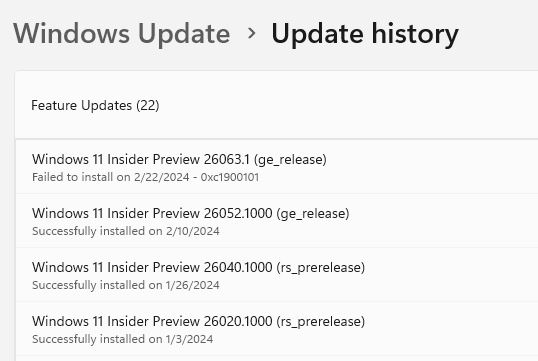
On January 8, 2024 Wi-Fi 7 went public. That’s the same day the Wi-Fi Alliance introduced its Wi-Fi Certified 7 program. USB4 version 2.0 goes all the way back to October 18, 2022. But only with the release of Insider Preview Canary Channel Build 26063 in February 2022 did MS start testing support for related Wi-Fi 7 drivers. (USB4 version 2.0 has been baked in since Build 23615 in the Dev Channel, released January 11, 2024.) Neither has appeared in a production version of the OS. Thus, a valid question for Windows 11 Wi-Fi 7 & USB4v2 has to be: What’s going on? TLDR answer right now is “Not much just yet.” There are lots of good reasons why so please let me explain…
What’s Afoot with Windows 11 Wi-Fi 7 & USB4v2?
One way to look at this is from a market availability standpoint. Precious few devices for sale right now support either or both of these standards. As I write this item, I see exactly 2 network adapters (one USB, the other PCIe x4) that support Wi-Fi 7.Ditto for Wi-Fi 7 routers. I can’t find any laptops that offer built-in support for either standard just yet. Many new models are promised later in 2024, and could change that.
Though it’s being proclaimed as something of an oversight it’s really just a function of supply and demand. (See this Tom’s Hardware news item by way of illustration.) Basic economics and recent history with Wi-Fi 6 and USB4 version 1.0 show that it takes about two years for these new standards to make their way from introduction and into more general adoption. I don’t see this latest iteration as terribly different.
Shoot! I didn’t lay hands on my first PC with built-in USB4 capability until the Panasonic Toughbook FZ-55 showed up here at Chez Tittel late last year. Just before Christmas, in fact. If it takes that long to hit my hot little hands again, I’m looking into late 2025 before a personal encounter might happen.