Holy Moly! I’ve been enjoying the workout involved in getting PowerToys “Command Not Found” (CNF) facility installed on my PCs and VMs. My latest adventure has been dealing with what happens when the Command Not Found module is itself not found. It might not be recursive, but it is amusing. After numerous futile tries to fix the PowerShell Profile or change its associated path, I simply uninstalled CNF, then re-installed it afresh. That’s how I learned a do-over fixes persistent CNF error.
Why a Do-Over Fixes Persistent CNF Error
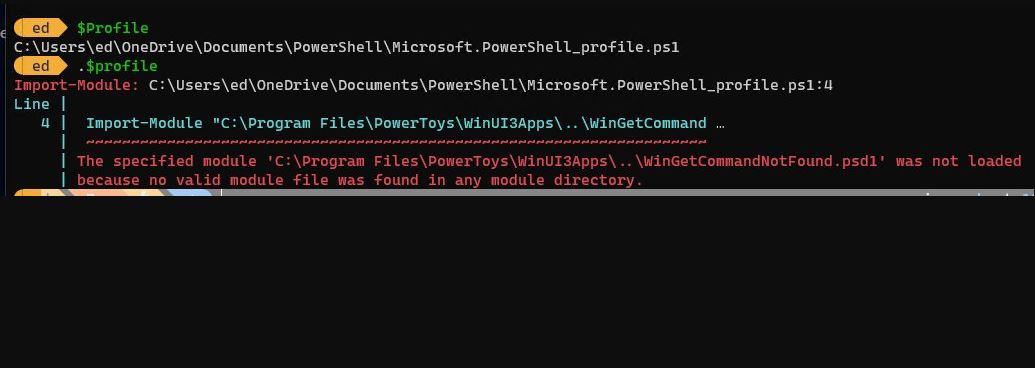
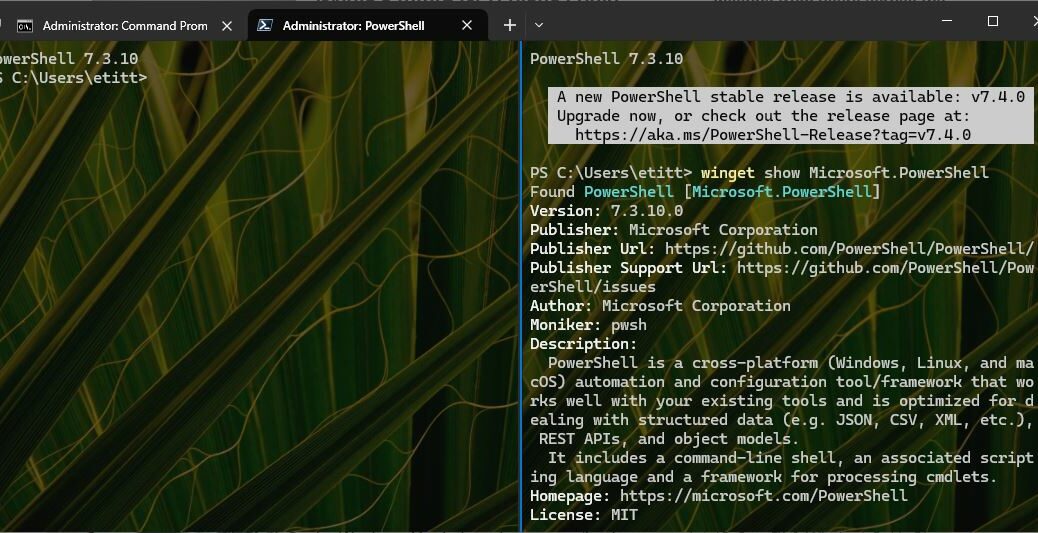
Examine the intro graphic above. It asserts that the CNF module “was not loaded because no valid module file was found in any module directory.” A search did turn up a module with the matching name (using Voidtools Everything) but something apparently went wrong with the file transfer, because this error message popped up anyway. I can only conclude that means it was invalid (inoperative). That said, all the PS path info on this machine matched that on my other PCs, so I’m confident it was never the problem.
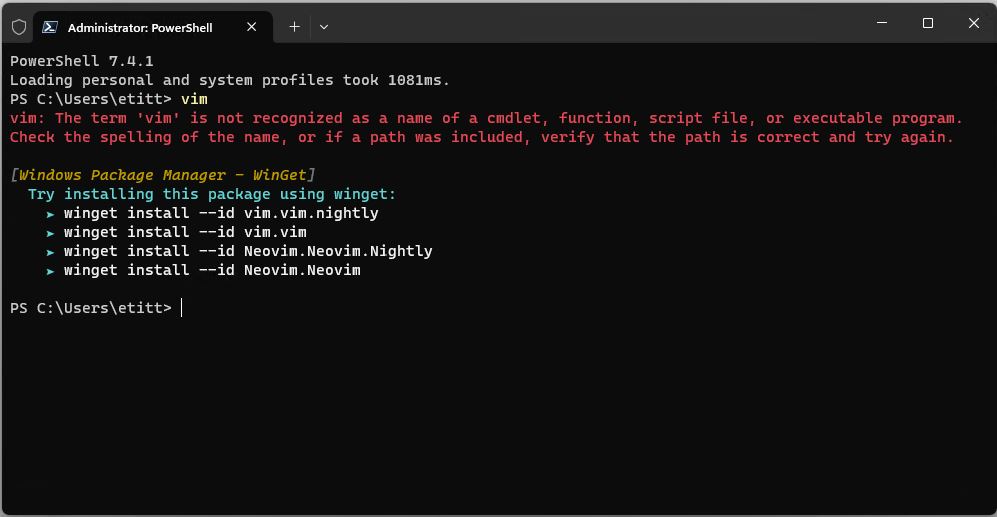
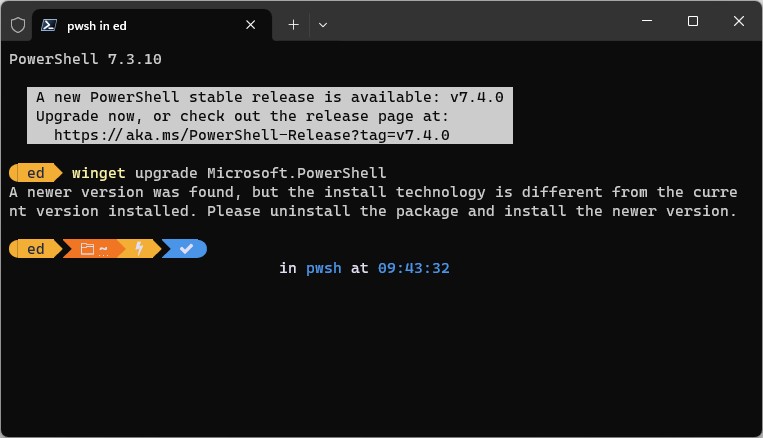
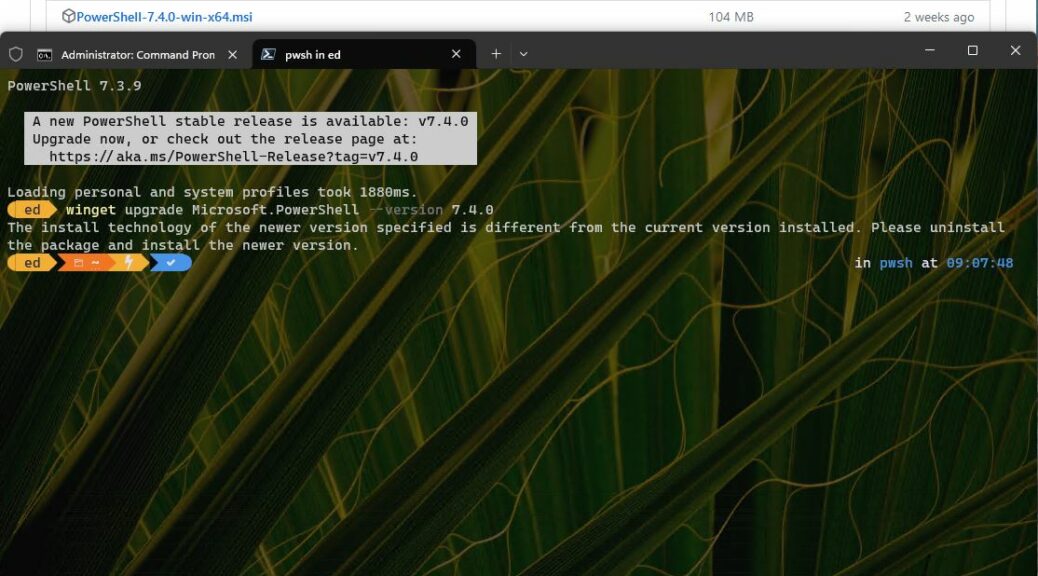
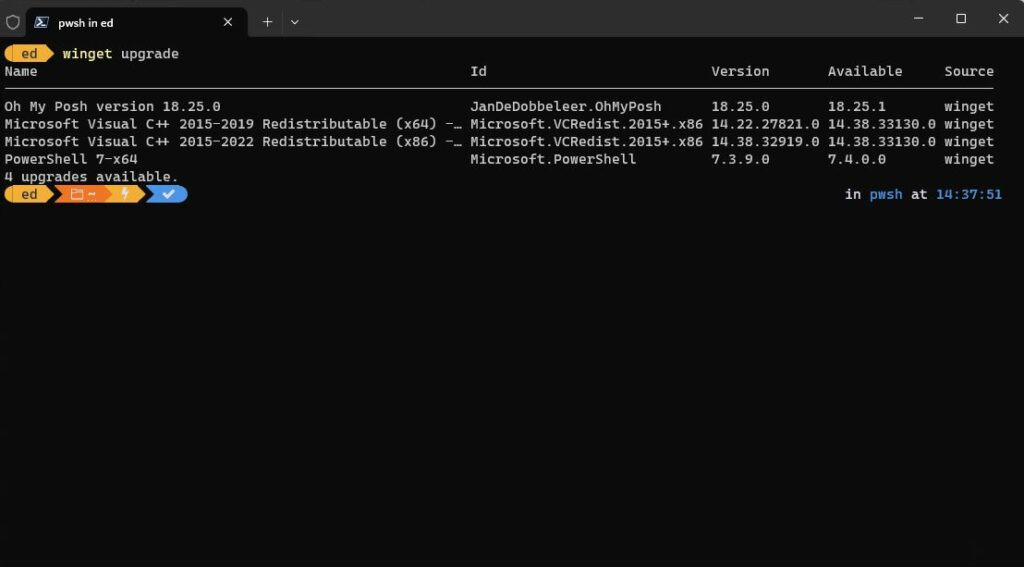
I’m pretty sure that’s why a do-over fixed things. When I uninstalled the munged version, all that stuff got deleted. When I installed afresh, the new copy of the module worked and the PS profile change did, too. As you can see in the next screencap it shows that the profile was loaded (top lines). Then I type “vim” to show that CNF intercepts this missing item and tells me where to go to find it. Problem solved!
The old “remove-replace” operation fixes baffling Windows errors. Here, you see profiles loading and CNF working after same.
[Click image to see full-sized view.]
There’s No School Like the Old School
In my three-plus decades of working with Windows I’ve seen my share of odd and interesting errors. Sometimes, things don’t work on the first try. But the uninstall-reinstall sequence — which I like to call the old remove-replace operation, hearkening back to my shade-tree mechanic days — will often fix otherwise mysterious and unexplainable errors or failures.
At least, it worked for me this time with the odd invalid module error for Command Not Found in PowerToys. A small triumph for common sense, here today in Windows World.