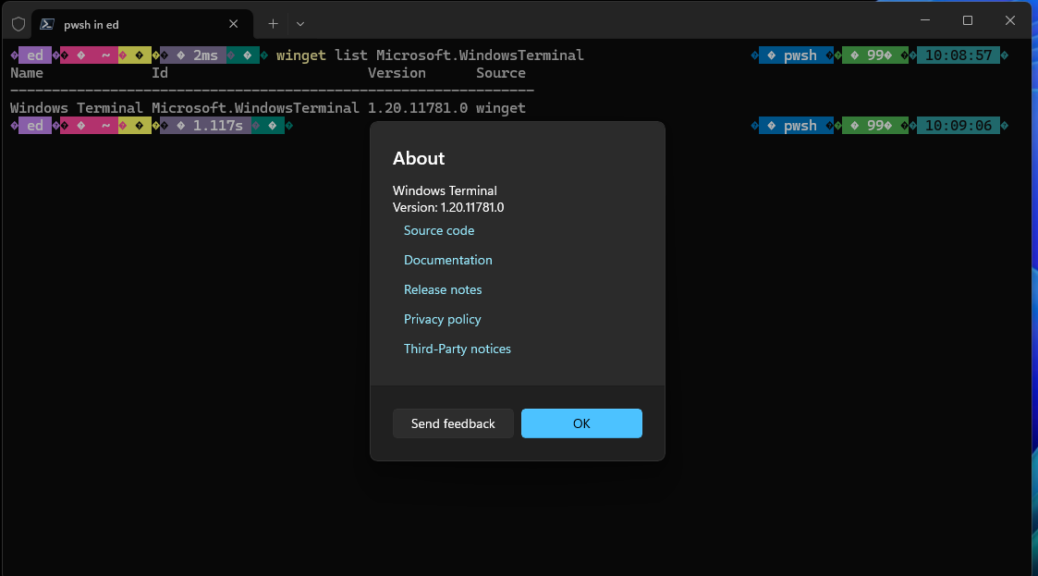
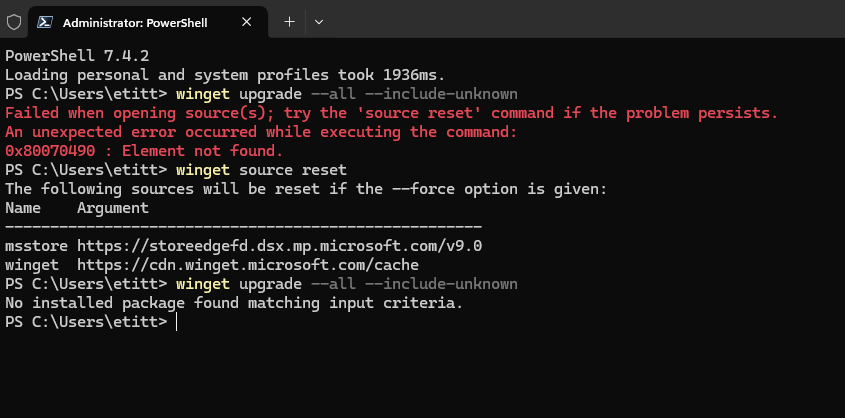
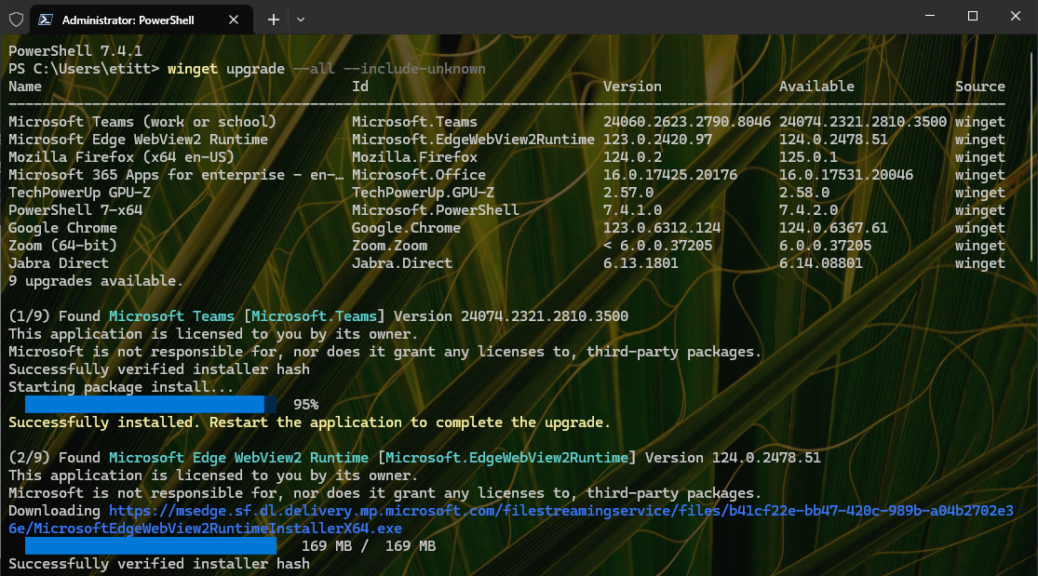
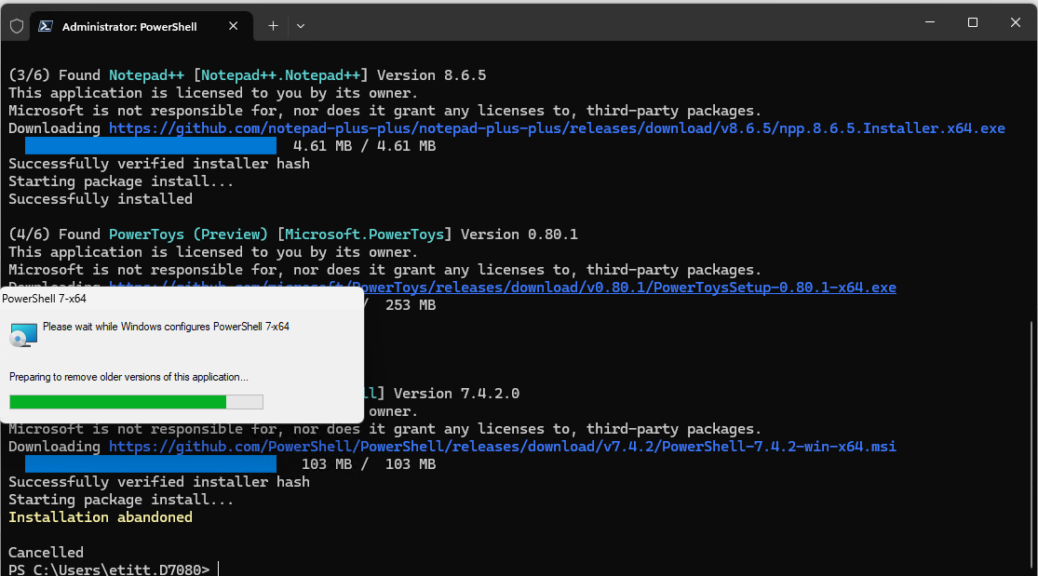
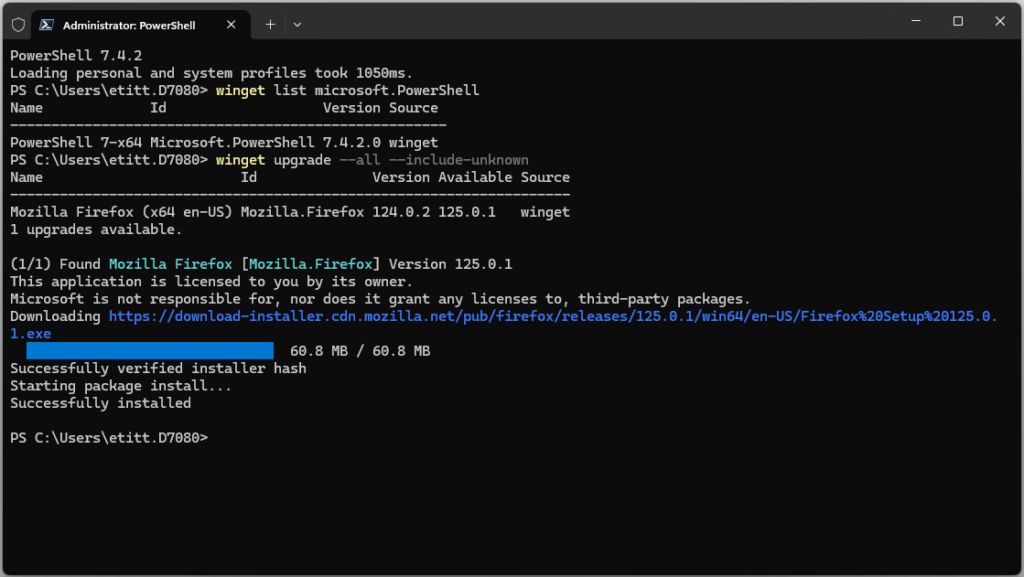
When I checked over the PC fleet this morning WinGet let me know an update for Windows Terminal was pending. It would take the program from version 1.20.11381.0 to 1.20.11781.0. Easy-peasey. But once is was done, I asked myself: what’s the best way to check that the new version is running. Thus, I found myself digging into how to update and check Windows Terminal versions. The lead-in graphic, in fact, shows two ways to version-check, captured from the colorful Lenovo Yoga Slim 7x Copilot+ PC.
For the record those two checks are:
1. Winget list Microsoft.WindowsTerminal shows the current installed version on the PC.
2. Click the down-caret in the WinTerm title bar, then click “About” from the pop-up menu to get the “About” mini-window atop the Windows Terminal application window.
How-to: Update and Check Windows Terminal Versions
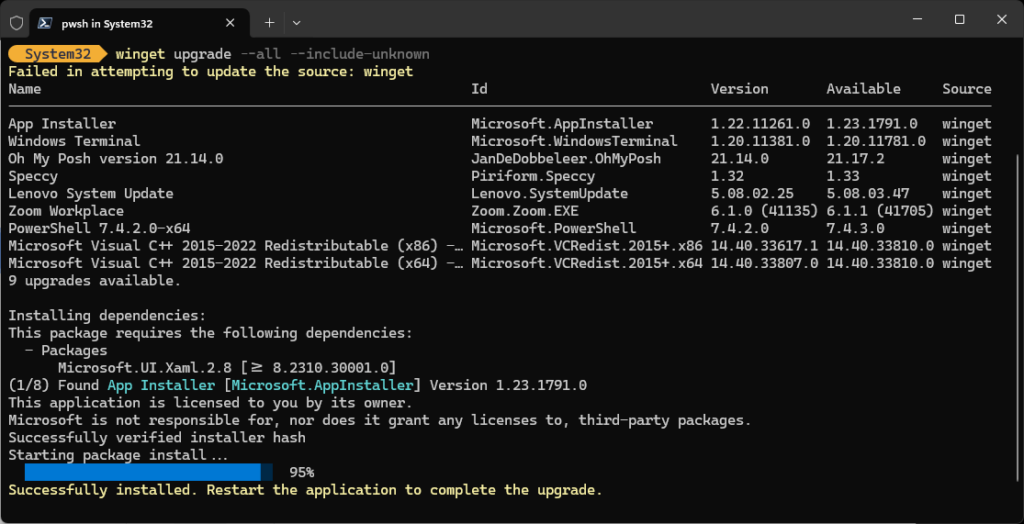
The update part is easy using the general WinGet upgrade –all –include-unknown command. But if you want to target WinTerm explicitly, Winget upgrade Microsoft.WindowsTerminal will also work.
One thing to remember, as you’ll see in the next screencap: once you’ve updated Windows Terminal, you need to close the current session, then open a new one. Why? Because the process that’s running the old version won’t quit, and a new process to run the new version won’t take over, until you’ve done the “out with the old, in with the new” routine that this accomplishes. Good stuff!
One more cool little detail: as soon as WinGet updates WinTerm, it bails back out to the command line. That’s so you can close/re-open your session and keep going…
Just another routine day here in Windows-World. I really enjoy working at the command line a LOT more, now that I’ve learned how to jazz things up and make best use of WinGet to keep them current.