Just over a month ago, I reached out to my contacts at Lenovo. I’d been wanting to lay hands on some newer PCs so I could dig into Thunderbolt 4 and USB 4 to understand its workings. A couple of weeks ago, I received a P360 Ultra SFF PC equipped with 2 each TB4/USB4 ports. Last Friday, unannounced and unexpected, another so-endowed laptop arrived at my door. Here, I’ll report on my initial findings as this Lenovo P16 Gen1 gets unboxed and set up. It’s a doozy!
Details: Lenovo P16 Gen1 Gets Unboxed
I’ll provide a recitation of facts and figures for this powerful portable workstation PC. In fact, it’s the most expensive personal computer I’ve ever worked on. Indeed, its website price, as configured, is a staggering US$9,719! It’s a big heavy sucker, too: 30.23mm x 364mm x 266mm / 1.2″ x 14.3″ x 10.5″, and 6.6 lbs/3.0 kg.
Here’s a selective list of what’s inside this beast of a Widows 11 Pro laptop. (Find all details on its product page under “Tech Specs”):
CPU: i9-12950HX (16 cores, 24 threads)
RAM: 128 GB (4 x 32GB 4800 MHz DDR5)
GPU (built-in): Intel UHD 770
GPU (discrete): Nvidia RTX A5500 (16 GB VRAM)
Display: 16.0″ WQUXGA (3840×2400) OLED touchscreen
SSD: 2 TB Kioxia KXG7APNV2T04 (PCIe 4.0 Gen4 NVMe)
Biometrics: Fingerprint reader and Hello IR Camera
As cool and impressive as all this stuff is — and it is all that for sure — the real reason I’m using this monster appears in the next image, enumerating the unit’s various ports:

My real reason for using this laptop is item 10, boxed in red.
[Click image for full-sized view.]
I’m jazzed, of course, by the panoply of features and stuff on this giant luggable PC. But I’m most interested in working with its two rear USB-C ports, both of which support Thunderbolt4 and USB4. And indeed, I’ve confirmed that both work as claimed. That’s not always the easiest or most obvious thing, as I’ll explain next.
Getting to TB4/USB4
As I’m learning, it takes some diligence to get either or both of these fast bus technologies to work. The PC port has to support these technologies, as does the target device, and the cable between the two. This is not always the easiest thing in the word to ensure or arrange. But as the following screenshot shows, I’ve gotten both working on the ThinkPad P16 Gen1 Mobile Workstation:
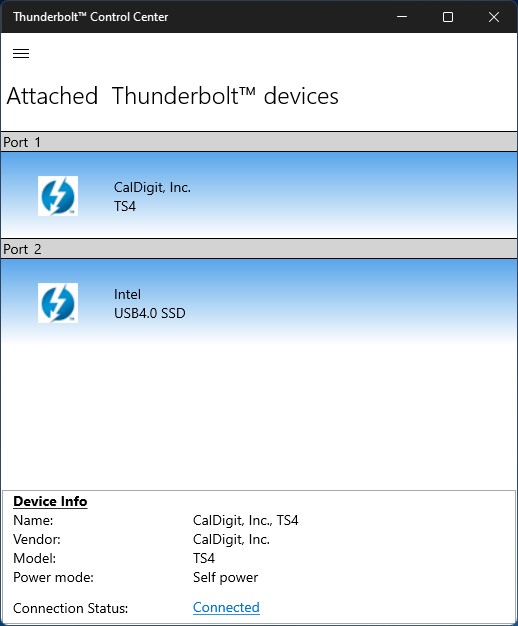
Intel TB Control Center: Above, the CalDigit TS4 dock; Below: an NVMe drive inside the Konyead USB4 enclosure.
[Click image for full-sized view.]
Both TB4 and USB4 remain cutting edge connection types. Everything about them is expensive right now. The CalDigit TS4 dock goes for over US$350 when you can find one for sale. The Konyead M.2 USB4 enclosure costs US$130, which is about what I paid for the Sabrent 1TB Rocket 4 Plus I put inside.
And then, one MUST use TB4/USB4 cables which aren’t cheap either (I got mine with the CalDigit) but they routinely go for US$20-40 for 1 M. Cables are not always well-labeled. It’s a good idea to go for those explicitly specced out for 40Gpbs data and marked as such. I’ve had lots of interesting issues from using lower-spec cables. Mostly, USB4/TB4 simply doesn’t work as promised and the device drops to UASP/USB 3.1/2 levels of performance.
Tomorrow, I’ll follow up and explain what all that means… Stay tuned!