OK, then. I finally laid hands on my second USB4 NVMe SSD enclosure yesterday. I deliberately sought out the cheapest one I could find so I could compare it to a more expensive alternative already on hand. When I say that USB4 delivers consistent NVMe performance here’s what that means:
1. The same SSD, cable, and host PC are used for comparison. Both drives have the “cache tweak” applied (this Oct 14 post has deets). Same tests performed, too (CrystalDiskMark and a Macrium Reflect backup).
2. The only thing that changes is the enclosure itself.
In short, I wanted to see if spending more on hardware returned a noticeable performance advantage (I’ll talk more about this below). Long story short: it doesn’t seem to make much, if any, difference. Let me explain…
Why Say: USB4 Delivers Consistent NVMe Performance?
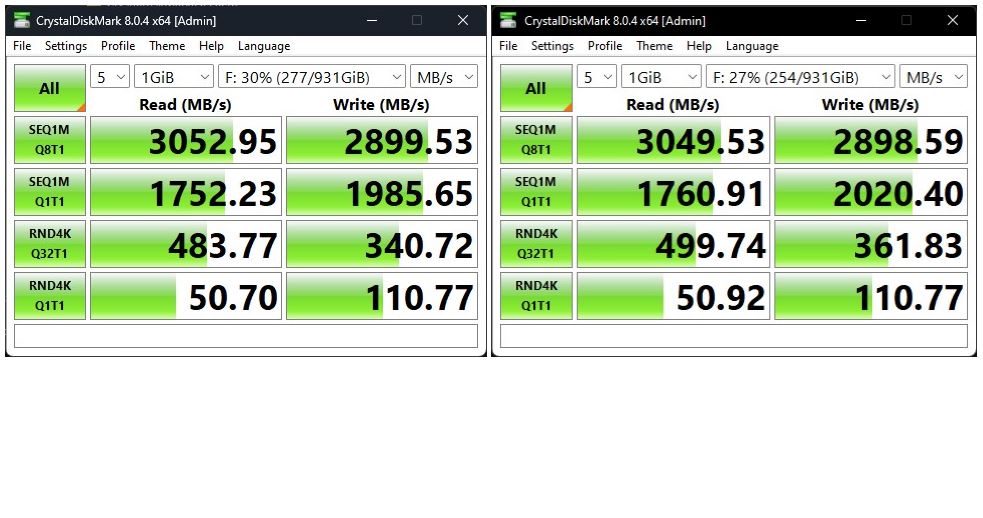
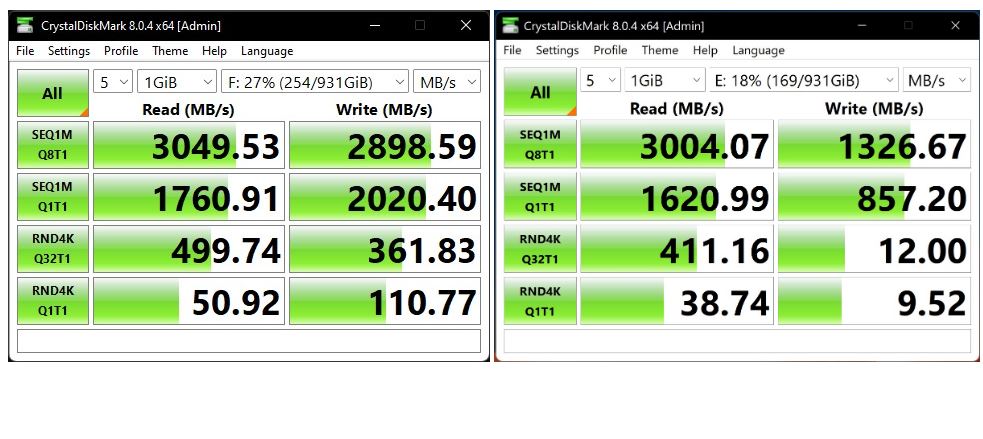
The lead-in graphic shows the results from the cheap enclosure on the left, and the more expensive one on the right. The average difference in CrystalDiskMark performance shows 2 wins for el cheapo, 5 wins for the higher priced item, and 1 tie. On first blush, that gives the more expensive device an advantage. So the next question is: how much advantage?
This is where a little delta analysis can help. I calculate that the average performance difference between devices varies from a high of 6.2% to a low of 0.03% (not including the tie). That said, the average performance difference across all cells is merely 1.54%. (Calculated by taking absolute value for each delta, then dividing by the number of cells.) That’s not much difference, especially given the prices of the two devices: $128.82 and $140.71. That delta is 8.4% (~5.5 times the average performance delta).
I will also argue that comparing CystalDiskMark results is interesting, but not much of a real-world metric. Thus, I’ll compare completion times for a Macrium Reflect image backup on the same PC, same OS image. The expensive device took 2:25, the cheap one 2:44. That’s an 11.5% difference, greater than the price delta but not amazingly so.
Deciding What’s Worthwhile
I can actually see some differences between the two enclosures I bought. One thing to ponder is that NVMe drives tend to heat up when run full out for any length of time (as when handling large data sets, making backups, and so forth). I’ve seen temps (as reported in CrystalDiskInfo, reading SMART data) go as high as 60° C while M.2 SSDs are busy in these enclosures. At idle, they usually run at around 28° C. The more expensive NVMe enclosures tend to offer more surface area to radiate heat while active, so that’s worth factoring into the analysis.
But here’s the deal: I can buy a decent USB3.1 NVMe enclosure for around US$33 right now. The cheapest USB4 NVMe enclosure I could find cost almost US$96 more. That’s a multiplier of just under 4X in price for a device that delivers less than 2X in improved performance. Let me also observe that there are several such enclosures that cost US$160 and up also on the market. I still have trouble justifying the added expense for everyday use, including backup.
There will be some high-end users — especially those working with huge datasets — who might be able to justify the incremental cost because of their workloads and the incremental value of higher throughput. But for most business users, especially SOHO types like me, the ouch factor exceeds the wow value too much to make it worthwhile. ‘Nuff said.