Although it showed up two weeks ago, yesterday was the first day I had open enough to unbox and bring up a brand-new ThinkPad. It’s a svelte (thin-and-light, in fact) 13″ laptop with an Intel Core Ultra 7 255U CPU, 16 GB RAM, Hello-capable IR camera and fingerprint reader, WUXGA (1920×1200) IPS 13″ display, and 512 GB PCIe x4 NVMe SSD. As configured, the Lenovo Store price for this unit is $1,269.33 this morning. As the ThinkPad X13 Gen 6 first look gets underway, I’m looking for answers to these questions:
1. Is this a Copilot+ PC?
2. What kinds of users is the X13 best suited for?
3. How does the unit perform on basic tasks? more demanding ones?
Digging in For a ThinkPad X13 Gen 6 First Look
Let’s answer those questions:
Copilot+ PC Status
The Intel Core Ultra 7 255U does have an NPU but it delivers only 12 TOPS. Copilot+ requirements call for 40 TOPS. So no, the X13 Gen 6 is NOT a Copilot+ capable PC. That’s not shocking — right now only about 1 in 50 laptops sold globally is Copilot+ capable (Copilot says it’s 1.9% of global PC sales, and 2.3% of Windows PC sales).
Who’s the Target Audience?
Based on the unit’s size, weight and configuration it’s an entry to mid-level laptop, designed for portability over power and capability. With a smallish 13″ screen, overall dimensions of 29.93 x 20.7 x 0.99-1.78cm / 11.78 x 8.15 x 0.39-0.7″, and a weight of merely 2.03 lbs (0.92 kg) it’s clearly a grab-and-go unit from start to finish. To me, that aims it squarely at an audience that needs computing mostly on the go, but not a whole lot of it.
IMO, that means this laptop aims at students, mobile office workers, and SOHO workers who need to pick up and carry it around rather than sitting always at the same desk. OTOH, this makes it an excellent “road machine” for users who want to carry something light and compact when they travel, but who may not use this laptop as their primary work PC.
Task Performance
Given its relatively modest processing, storage and memory endowments, the X13 Gen 6 configuration I examined — and the whole product line, in fact — aims to support users who want to surf the web, read e-mail, and handle routine productivity, media, and entertainment workloads. I wouldn’t recommend it to those who need to run large or demanding workloads including serious programming, local AI models or other big datasets, or heavy-duty 3-D graphics (which knocks it out of consideration for media, gaming, CAD/CAM, and so forth). If you want more performance nuts-n-bolts see this July 2025 review at Gigazine.
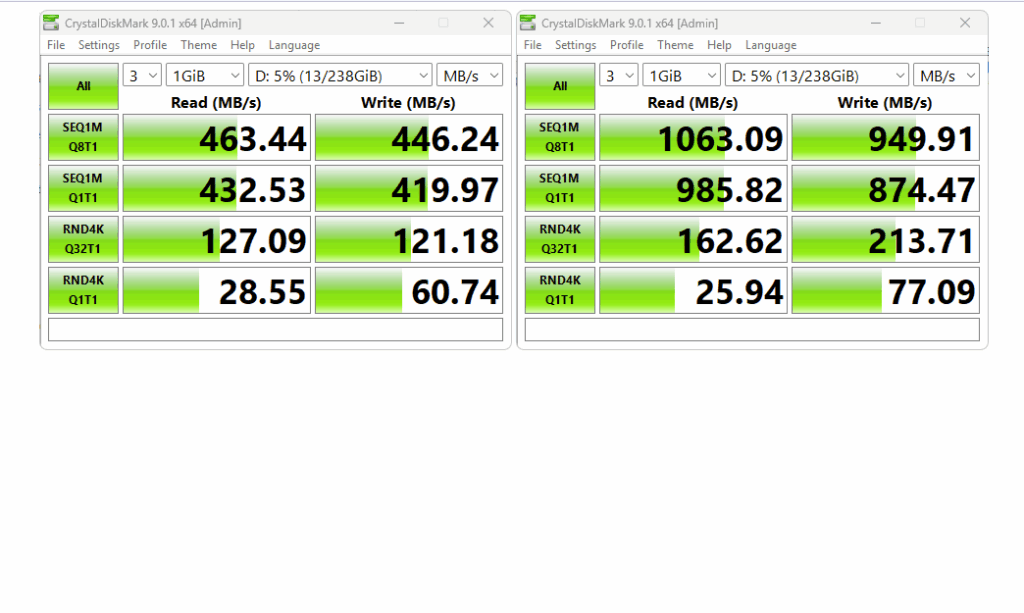
The built-in NVMe is a Lenovo model RPETJ512MMW1MDQ (M.2 22380 with Gen3/Gen4 level performance. It’s reasonably quick, but nowhere near state of the art. The unit relies on a built-in Intel graphic processor in the Xe-LPG family. It’s designed to run on par with entry-level discrete GPUs, and thus, to handle light gaming, media editing and AI workloads. Squares entirely with my subjective impression in watching YouTube, installing and using apps, and bringing the PC current with WU.
Initial Impressions: Nifty, Not Gnarly
The unit itself is incredibly light, but feels sturdy and looks good. I didn’t feel much flex in the keyboard or monitor decks as I picked it up and moved it around. The Windows Hello capable IR camera and fingerprint reader are both fast and easy to set up. Amusingly, I found it difficult to switch from my primary MSA to other accounts at login after I’d set the camera up, because it would log me in faster than I could click the lower-left icon for an alternate account at startup.
I couldn’t log into my ASUS AX-6000 802.11ax router on the 5GHz channel for some reason or another. The unit’s Wi-Fi6E Intel worked just fine with the 2.4 GHz channel, and performed well as I downloaded and installed a raft of updates and software apps.
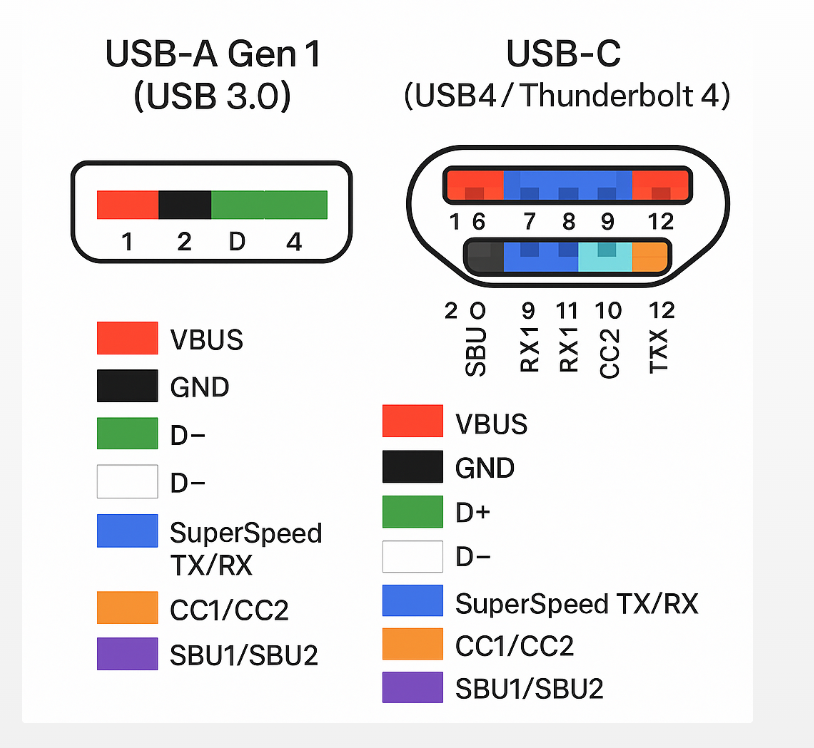
The X13 has 2 USB-C ports, one of which goes to power unless you dock it up and get power that way. Both are USB4/Thunderbolt 4 capable. It also has 2 USB A 3.2 Gen 1 (5 Gbps) ports as well, along with HDMI 2.1 and 3.5mm audio (mini-RCA jack). It’s not overly endowed with ports, but they are sufficient for ordinary users’ needs.
First Look Takeaways…
Overall, this is an eminently portable and usable light-duty laptop. I’d buy one for my about-to-graduate college offspring, except I opted to spend $450 less to buy him the Lenovo Yoga Slim 7X Copilot+ laptop in May. It lacks USB-A and headphone jack, but offers longer battery life and better AI capabilities.