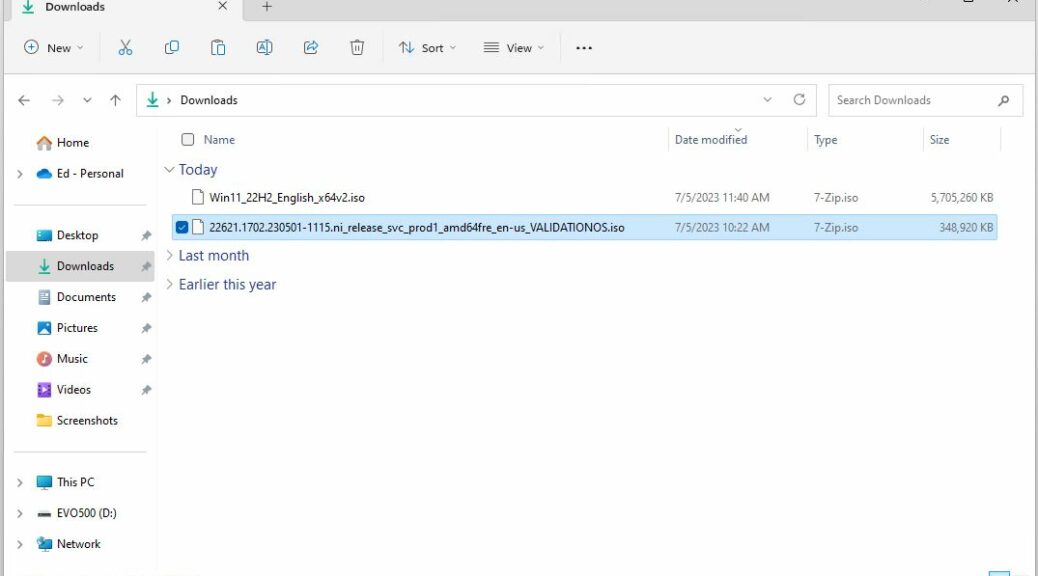
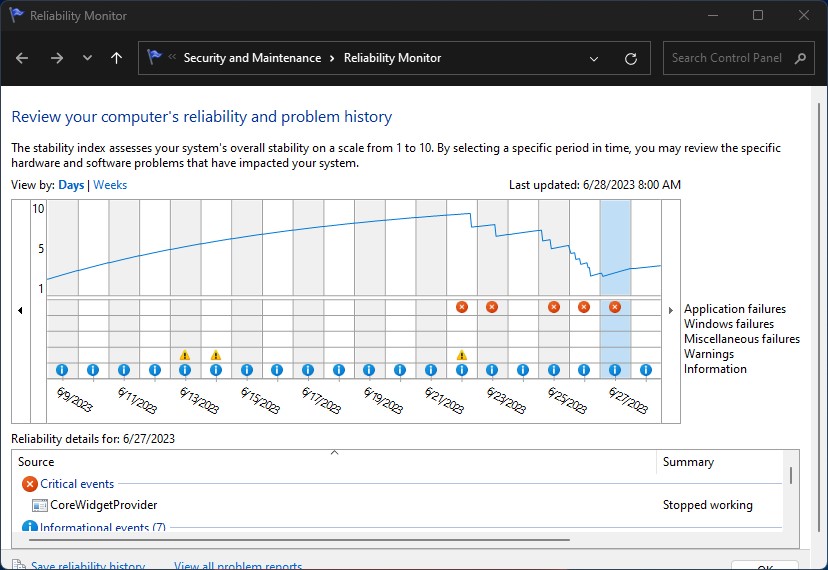
Here’s something new to me that’s apparently been a thing for some time now. It’s called a “Validation OS” and includes an image file named ValidationOS.wim. When I tell you it’s a mere 193 MB in size and represents a (mostly) read-to-run image for Windows 11 22H2, that should raise your eyebrows. By comparison the 22H2 Download from the Download Windows 11 page weighs in at 5.4GB! One key point in understanding Windows validation OS is that it’s minimalist and limited by design. That’s why I show adjacent file listings from the Explorer Download folder as the lead-in graphic here.
Overview: Understanding Windows Validation OS
Here’s how MS describes this Windows 11 OS version and its purpose (from MS Learn’s Microsoft Validation OS documentation; bold emphasis mine):
Microsoft Validation OS is a lightweight, fast, and customizable Windows 11-based operating system that you can use on the factory floor to diagnose, mitigate and repair hardware defects during Windows device manufacturing. Validation OS boots into a Command Line environment to increase reliability on the factory floor and supports running Win32 apps, smoothing the transition from early hardware bring-up to retail OS and apps development.
The Validation OS offers only a command line interface as delivered. But by using DISM to operate on the .wim file you can add whatever packages you like to this bare-bone OS image. The list of optional packages available for use with this image includes (paraphrased from the afore-linked) Validation OS reference at MS Learn:
- PowerShell: provides PS and basic modules/cmdlets
- Basic connectivity (HID, USB and Serial device connections)
- Disk tools (built-in Windows disk tools, including diskpart.exe)
- GDI Plus: add graphics capability through GDI Plus support
- .NET Framework 4.5: permits use of basic .NET features
- Plug and Play: provides support for plug-and-play devices
- Windows Device Portal: lets OS access WDP server for driver downloads
- Other drivers: by class, includes memory, core system extensions, network drivers, and more
What the Validation OS Good For?
It is intended for developers and OEMs to provide a quick-to-boot-and-run, lightweight version of Windows 11 they can use to test specific hardware configurations. Developers can use it to simplify and speed up driver creation and maintenance.
But gosh, a lightweight version of Windows 11 is also handy for rescue and recovery purposes, too. Those who know how to use DISM will be able to use its add-package capabilities to extend and customize this Windows image (it will also be necessary to take this approach for updates as well).
This one’s definitely worth exploring and possibly putting to work, for admins who test configurations and updates prior to deployment, and for anyone in search of a good starting point for a customized, bootable repair/recovery environment.
Note: here’s a shout-out to Sergey Tkachenko at WinAero, whose July 4 story “Microsoft’s Validation OS Again Received and Update (Quietly)” clued me into this version of Windows 11. Thanks!