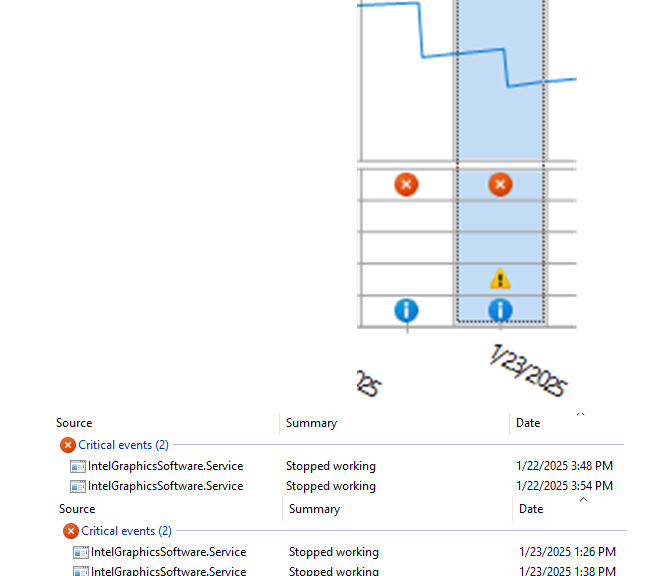
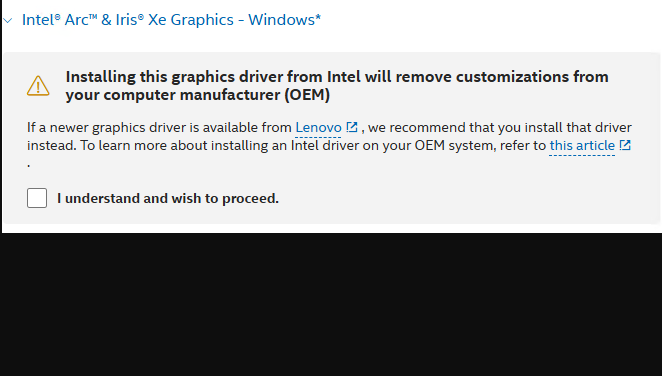
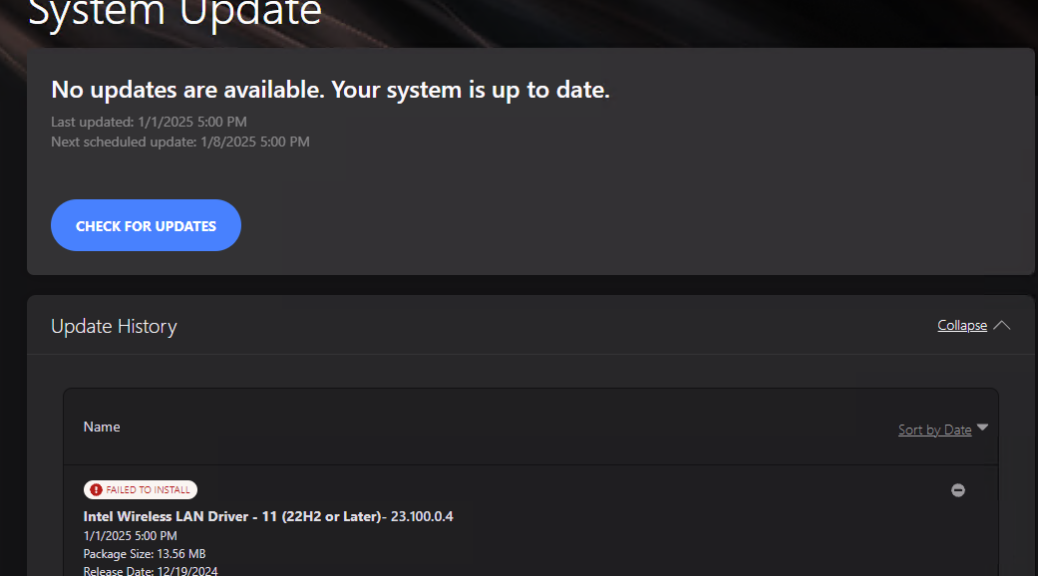
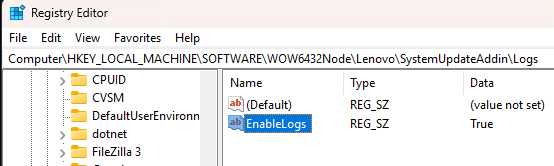
It’s a classic trade-off in more ways than one: cost versus speed. I’m prepping for an AskWoody story about external media on Windows PCs. For me, the big trade-off when considering USB4 external media is higher prices for higher performance. “How much higher?” you ask: that’s what I’m in the process of figuring out right now.
Whole Device Chain Counts When Considering USB4 External Media
Every step in the device chain counts when going for the speediest external Windows media. The starting point from the PC end is the USB port itself. Ideally, it should be USB4 or Thunderbolt 3/4, and support 40 Gbps throughput. Next comes the cable: it should be labeled USB4, Thunderbolt 3 or 4, or 40 Gbps. Next comes the storage device. For me, that mostly means an enclosure housing an NVMe SSD. That enclosure should be USB4 or Thunderbolt 3/4, and the NVMe should be Gen 3 (PCIe x3) or higher.
At every step you pay more to attain the current pinnacle of performance. (I’ve not yet seen any 80 Gbps devices, but they’re coming. Copilot tells me Intel’s 14th Gen HX-series mobile CPUs “are starting to support this technology. “) A quick search at Amazon tells me you can’t buy USB5 cables, docks, and so forth yet. My best guess: we’re looking well into 2025 before it goes mainstream.
Right now, the jump from USB 3.2 Gen 2 (10 Gbps) to USB4 (and TB 3/4 equivalents) is getting cheaper, but still costs. You’ll pay US$46 for the cheapest USB4 M.2 enclosures right now (more like US$75 and up for other options). That’s double the cost — or more — of USB 3.2 Gen 1 devices (UASP: see below). Cables cost US$2 to $10 more for faster varieties, which isn’t too punitive. You can’t take advantage of anything faster than Gen 3 NVMes. Thus, you can buy 1 TB for US$55-80, and 2 TB for US$93-130 or so.
The “big spring” comes from the cost of either buying (for laptops and so forth) or installing (for desktops with open PCIe slots, and ASUS is the only vendor I can find who makes one for US$126) to gain a USB4 40 Gbps port to plug into. My testing so far shows this DOES make a difference, and often offers better performance than older and rarer Thunderbolt 3 or 4 capable USB-C ports.
For Me, Backup Is the Killer App
I’m always messing with PCs, so I need to back up frequently in case I shoot myself in the foot and have to replace a mangled installation. It happens to me at least 1-2 times a week in my testing and research, so this is no joke. I find the cost of USB4 external storage worthwhile because it drops the time to make a complete image backup into the 2-4 minute range. It takes anywhere from 7-24 minutes to back up to UASP-capable external storage. This equates to USB 3.2 Gen 2 10 Gbps capability. It shows up with max read/write speeds in Cystaldiskmark in a range from 1000-1100 MBps.
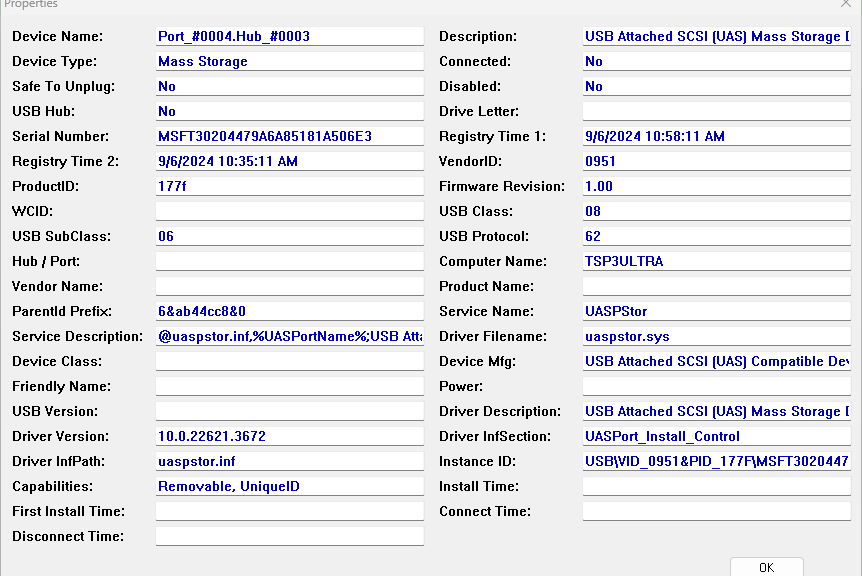
If you look at the lead-in graphic, which comes from NirSoft’s USBdeview, you can see it references the UASPStore.sys driver and service. I’ve actually found this to be a clearer way to recognize when a USB 3.x port can provide somewhat higher speeds. If your USB 3.x ports are older (and slower) they’ll usually show a USBstor.sys driver instead (and max speeds in CrystalDiskMark in the 400-500 MBps range).
You pays your money, and you takes your chances. That’s how things go with external USB-attached Windows storage — and much else in life!




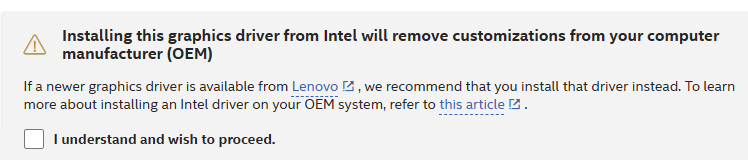 And indeed, now that I’ve uninstalled that driver and reverted to a Lenovo driver dated 10/29/2024, I’ve experienced no further issues with Intel graphics stuff. That said I do have an APPCRASH for the IntelSoftwareAssetManagerServer.exe process. But a quick hop to the Intel Support Community shows that this belongs to PROSet Wireless stuff not graphics. So there’s a problem for another day!
And indeed, now that I’ve uninstalled that driver and reverted to a Lenovo driver dated 10/29/2024, I’ve experienced no further issues with Intel graphics stuff. That said I do have an APPCRASH for the IntelSoftwareAssetManagerServer.exe process. But a quick hop to the Intel Support Community shows that this belongs to PROSet Wireless stuff not graphics. So there’s a problem for another day!