It’s always a humbling experience to work and work with Windows. This week, I’ve been relearning how Windows 10 works with Windows Terminal (and sometimes doesn’t). I had to stand up a squeaky clean Windows 10 instance in a VM for some WT testing and research. Tongue planted firmly in cheek as I went through some recent Windows Terminal follies, I realized I’d forgotten more about WT than I’d ever known. Let me explain…
History Underlies Recent Windows Terminal Follies
Today, my production Windows 10 installation has been running since 2016, when I stood up my present primary desktop PC. There have been a LOT of changes to Windows since then. And indeed, Windows Terminal (WT) is one of the things that has changed the most. But because I’d gone along with those changes — growing more experienced and wise to the ways of WT — I really didn’t remember all of the little twists and turns along the way.
Thus, installing a clean Windows 10 OS image came as a series of shocks where WT was concerned. Let me list a few of them:
1. Windows 10 made its Insider Preview debut in 2014, WT didn’t come along until May 2019. Thus, it’s not set as the default command line environment in Windows 10.
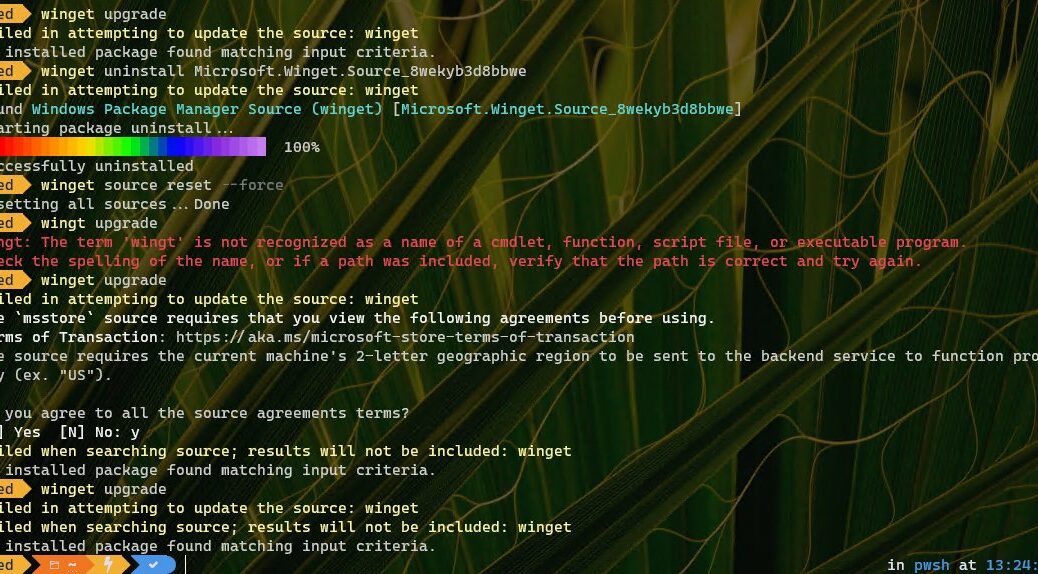
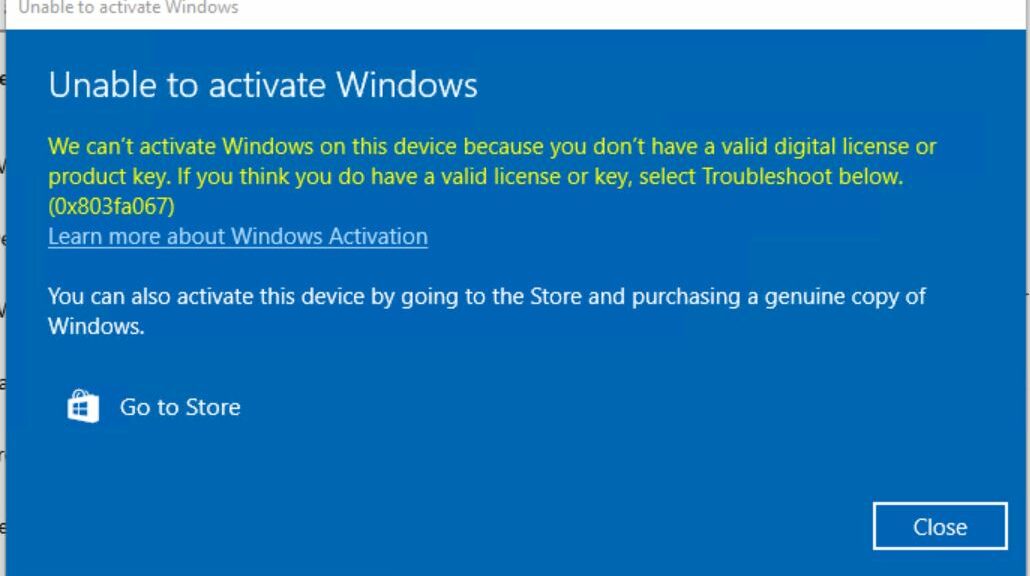
2. WinKey+X, to my consternation, kept launching an older PowerShell version (v5.1.19014.3570). And the only version of WT present was an older Preview that I didn’t want.
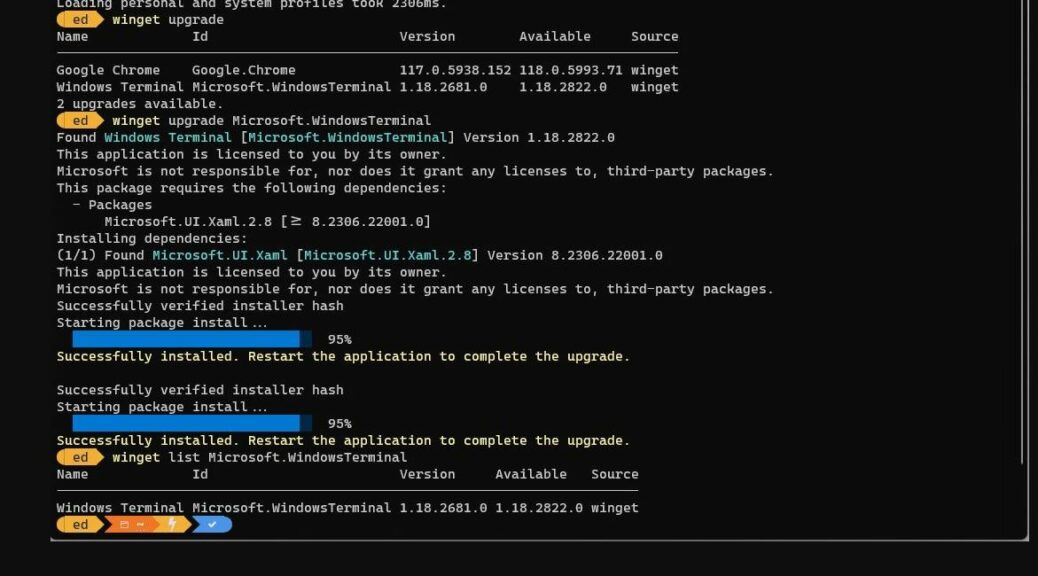
3. Thus, I found myself visiting the MS Store to grab the latest copy of WT, installing it, then setting it as my default terminal application (see lead-in graphic: notice further than this version needs an upgrade).
Eventually, I got things sorted and where I want them to be. But it did come as something of a shock to understand how much change I’d been introducing to my desktop runtime, step by little step. Only when I had to jump the whole stretch in a single bound did I see how far things has really come.
Some Unexpected MSA Bonuses Also Present
OneDrive picks up files from my User folder as part of what it keeps in the cloud. Apparently this includes my PowerShell Profile, because an invocation to OhMyPosh showed up as I fired off the new WT install for the first time. That made setting up OMP even faster and easier than usual.
The moral of today’s story is that one doesn’t really recognize how far one has come (or how much things have changed) until one is forced to recover the same ground and see what’s different. That’s one good reason why — for me, at least — Windows-World is always an adventure.