Deja vu! With the introduction of version 7.4.0, MS once again changed the PowerShell (PS) installer. That means Winget won’t update PS directly; one must visit the GitHub PS page and grab a new installer from there. Afterward, as shown in the lead-in graphic, old(er) version(s) of PS still show up when WinGet upgrade is run. Fortunately this recurring PowerShell update issue is easily fixed. Let me explain…
Fixing This Recurring PowerShell Update Issue
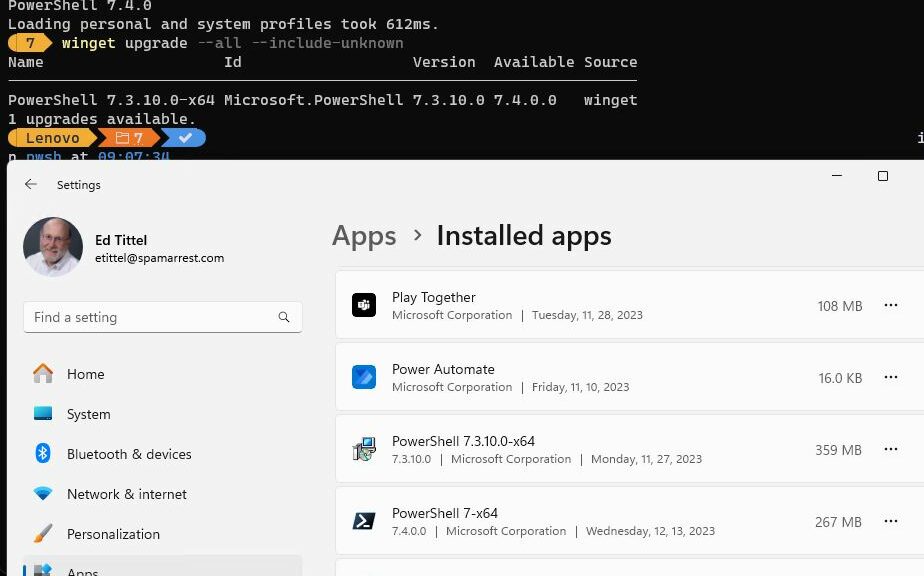
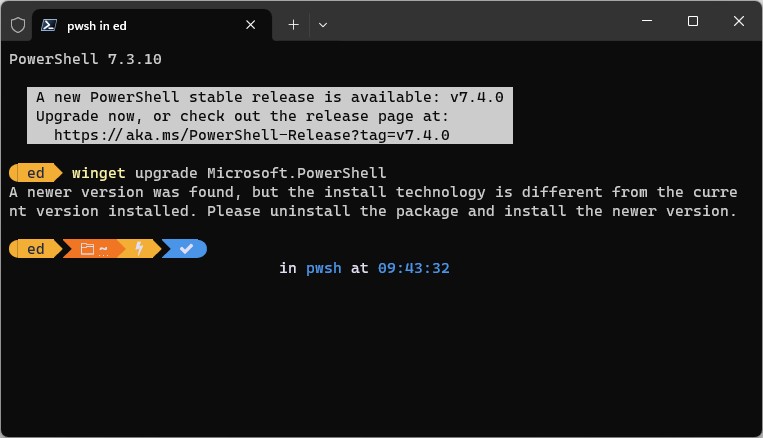
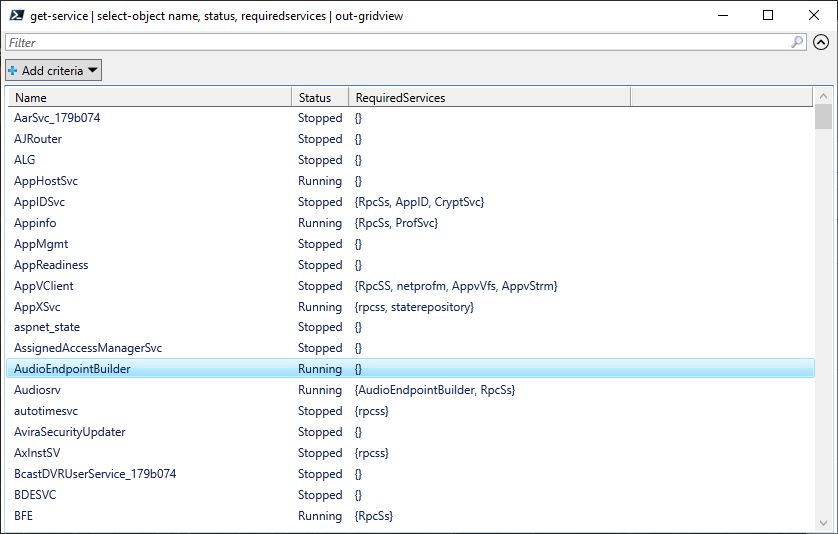
Take a look at the lead-in graphic. It shows a single upgrade to PowerShell, from version 7.3.10 to 7.4.0 is available. But when I try to use winget to do the job, it reports a change in installer methods and won’t handle this task. This requires a trip to GitHub (the whole process is described in my November 17 post) to grab and install PS using its Microsoft Installer (.MSI) file instead.
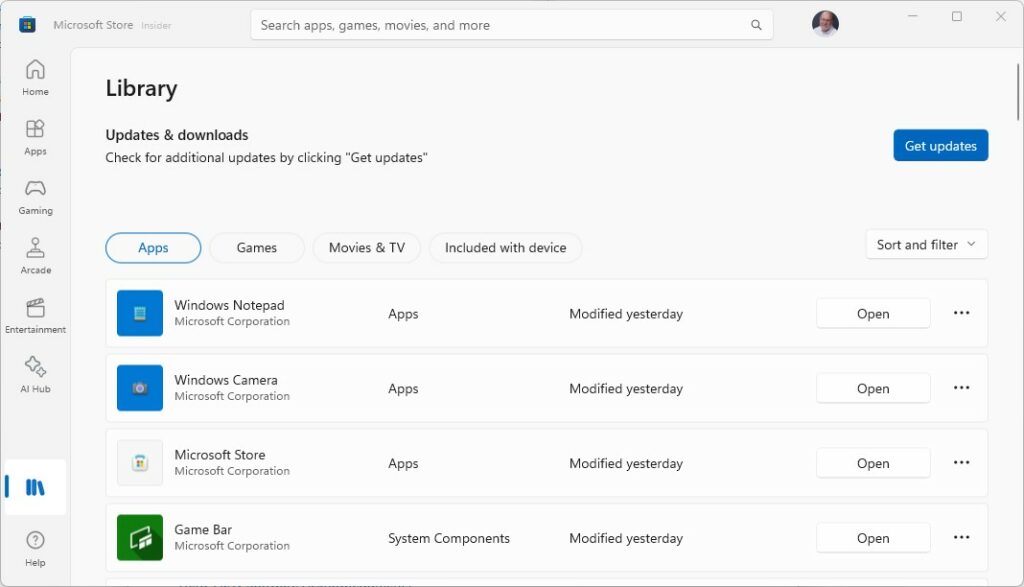
But there’s a catch: as you can see in the Apps portion of the lead-in graphic, the PS installer does NOT clean up older versions. Thus, not just one, but two older versions of PS show up therein — namely 7.3.10 and a 10/25/2023 Preview version. Winget will report that the 7.3.10 version needs an update because 7.4.0 is available. Thus, you need to uninstall that version to stop this warning.
So that’s just what I did. And because I’m not using the PS Preview any more, either, I uninstalled it too. Problem solved. But here’s a request to the PowerShell team: please add a check for older stable versions (e.g. 7.3.10 in this case) and offer to uninstall it during the new stable version install process. It would make life ever so much easier, thanks!
Fingers crossed that they agree. I’ll be sure to copy this to the winget and PowerShell teams leads when I tweet this item out later this morning, too. That said, the new PS window notification does instruct users to “uninstall the package and install the newer version” so maybe they’re not interested in tackling this job. We’ll see…
I can’t say MS doesn’t warn users. I can say I didn’t see it right away, though…