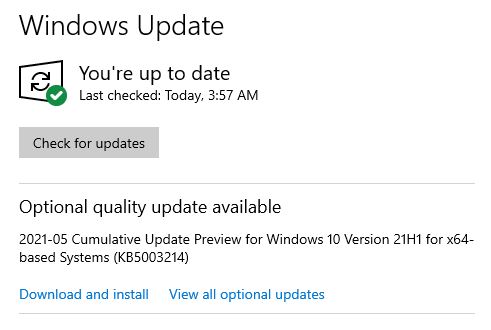
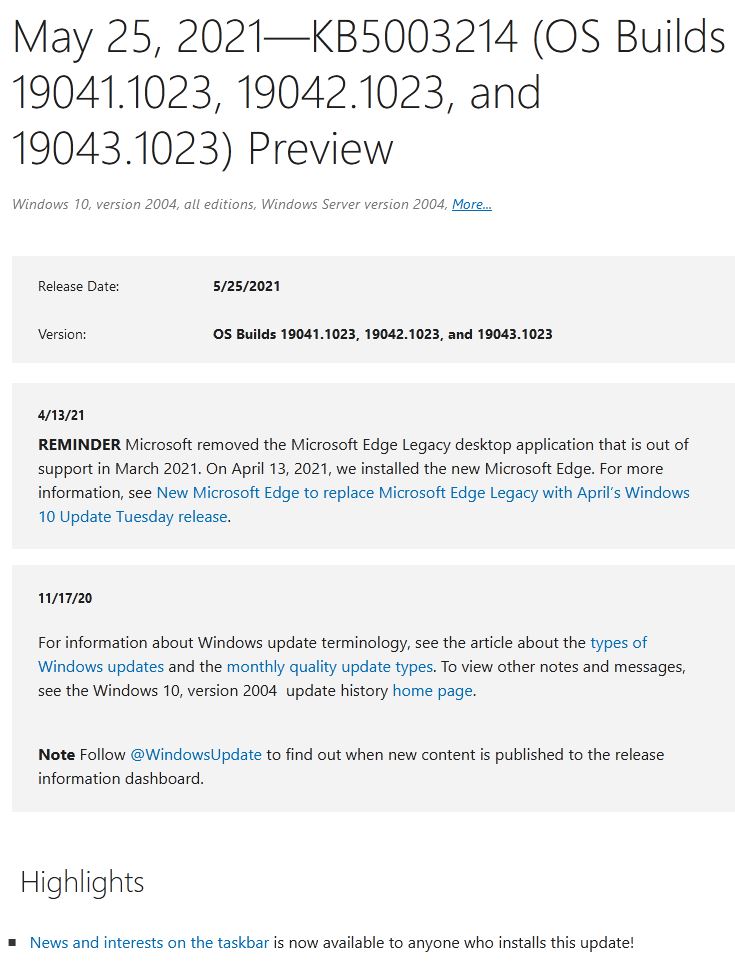
Normally, many people steer clear of late-in-the month Windows update offerings. That goes double for KB5003214, which is a non-security CU (cumulative update) Preview update. Please let me suggest a reason to over-ride such natural and eminently sensible hesitation. This update brings the News & Interests taskbar/notification area mainstream into current Windows 10 versions 2004, 20H2 and 21H1.
This morning, after installing KB5003214 on my production PC, I had the pleasure of seeing the News & Interests “bug” show up at the right-hand side of the taskbar, like this:
It may not look like much, but you can expand it by clicking, and it’s been a long time coming.
If Build 19041/2/3.1023 Brings News & Interests Mainstream, Install It!
Personally, I’d been on the B side of Microsoft’s protracted A/B testing for this feature on Dev Channel and other Insider Preview builds. Thus, I couldn’t wait to see it go mainstream. It’s popping up on production desktops at Chez Tittel right now like mushrooms after the rain. (FWIW, we’ve had plenty of rain around here lately, too!)
If you look to the bottom of this screencap from the KB5003214 release notes header, check the first highlight. It proclaims “News and interests on the taskbar is now available to anyone who installs this update!” Need I say more? Surely, that’s worth jump-starting normal practices and installing a preview CU to see.
Jump to the bottom for the News and Interests proclamation.
You tell me: is this a compelling reason to jump the gun, or not? I can only say I found it compelling. You’ll have to decide for yourself whether or not you want to download and install KB5003214, or wait for next month’s Patch Tuesday CU and get it then instead.