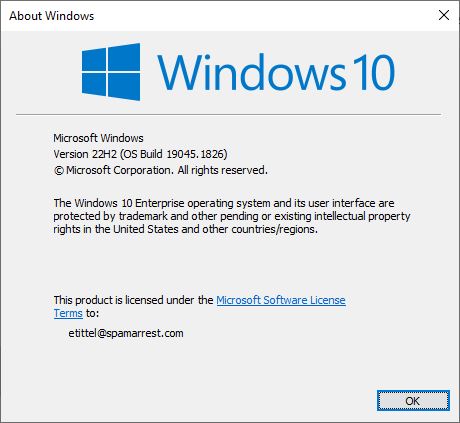
Here’s an interesting item. Turns out that MS has made KB5015684 available through its update servers. Thanks to the team at DeskModder.de you can find x86, x64 and ARM64 versions of either .CAB or .MSU files. All have links of the form https://catalog.s.download.windowsupdate.com/c/upgr/2022/07/windows10.0-kb5015684-xxx.cab or .msu. They must be legit, right? Hence my claim that KB501864 provides quick Windows 10 22H2 upgrade.
I just ran it on my production Windows 10 PC, and it went through without hitch or glitch. Completed in under 2 minutes, including download, install and reboot time, too. May be worth a try for those with Windows 10 PCs not expected to elevate to Windows 11 soon (or ever). So far, I see no discernable changes in look, feel, or behavior — just a new Build number 19045 (vs. 19044). Same minor extension as before, in fact: 1826.
What KB501864 Provides Quick Windows 10 22H2 Upgrade Really Means
Two things:
1. MS is getting close enough to a 22H2 public release for a preview to go out.
2. The code for the 22H2 release is stable enough to start it through the Windows Insider program.
Note: I didn’t have to join the Insider program to install this update, which appears as a “Quality Update” in Update History. The Windows Insider Program page on this PC, post-update, does NOT show itself as “joined-up” either. So one need not be concerned that applying the update automagically changes the PC’s status to that of an Insider machine. That’s a relief!
I ran the .MSU x64 version of the upgrade, simply because a self-installing update file is a little easier to apply than CAB files can sometimes be. You can find all links in the original Deskmodder.de article (6 files in all). It might be a good idea to apply this upgrade to test machines with some caution, if you’re concerned about possible unwanted side effects. That didn’t stop (or hurt) me on this PC, though…
If you’re interested, have at it. Cheers!