It’s been a struggle to get the latest Dev Channel Insider Build updated lately. I’ve already described how KB 5001030 and KB5003397 aren’t working on my test machines. Lately, Defender has been stuck as well. That’s how I learned that a Defender update download circumvents stuck 21364.
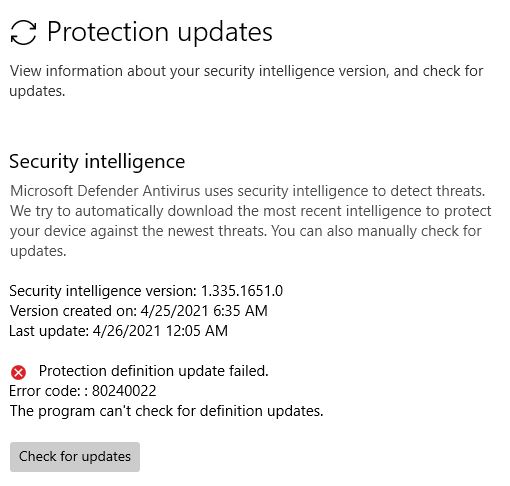
Normally, you can simply open the Windows Security item in Settings → Windows Update. Next, you can forcibly get Defender to update by clicking “Protection updates” under “Virus & threat protection updates.” Not this time! This mostly-infallible workaround throws an “update failed” error. It explains further it “can’t check for definition updates” (see lead-in graphic).
Shoot! I even tried the command line program MpCmdRun.exe. First, I cleared the Defender signatures (that worked). Then I tried to download a new set (that failed). This time, apparently update downloads are well and truly stuck. For the record neither the Update Troubleshooter, nor the TenForums WU Reset batch file worked, either.
Thus: Defender Update Download Circumvents Stuck 21364
Relief is available from the “Latest Security Intelligence…” MS Security Intelligence web page for Defender. I provide its URL because it’s more informative than that title: https://www.microsoft.com/en-us/wdsi/defenderupdates. If you scroll down this page, you’ll find a section entitled “Manually Download the Update.” Follow the link that matches your Windows 10 version and you’ll download a program named mpam-fe.exe.
If you run this program it will (a) update your Defender signatures, but (b) provide no interaction or feedback. That holds, even if you run the program as administrator. The only way to tell it worked is to check the timestamp for Last Update in Windows Security → Virus & threat protection under the “Virus & threat protection settings.” After you run this program, you’ll see a timestamp that reflects a the recent past. It’s too stealthy for my sensibilities, but it does work.
I’m OK without CUs and Such, But…
When update trouble rears its head on Insider Previews, I’ve learned to cope. I’ve also learned it’s essential to be patient when MS goes into “break-fix” mode. That is, when they acknowledge something is broken and promise to fix it “soon.” And to the Insider Team’s credit most such fixes come sooner rather than later.
But I can’t accept an inability to update Defender on my test machines, where’s its my only anti-malware defense. That’s why I’m glad I’ve now learned how to manually download and install signatures to keep safe, even when updates gets stuck, as they sometime do. So while they’re still stuck for 21364, I’ll use this web page to update daily just to be safe…
Note Added 6 Hours Later
Just for grins, I tried out the old Windows Update MiniTool (WUMT) on my stuck test machines. It was happy to download and install the Defender updates for me. But it did not “see” the two problem KBs until I resumed updates in WU. Acting on advice from the Insider Team that I should be able to install the .NET update, I tried that inside WUMT on my Lenovo X220 Tablet and X380 Yoga It reported it was downloading, then installing, for each of the two problem updates. But alas while KB5003397 succeeded on the X220 Tablet, it failed on the X380 Yoga. And KB5001030 worked on neither machine, even using WUMT. Go figure!