It’s that time of year again, when MS meetings and conferences — Ignite 2024, in this case — heat things up with future promises and new idea campaigns. Yesterday’s Windows Experience Blog from David Weston (MS VP Enterprise & OS Security) is a case in point. Entitled Windows security and resiliency: Protecting your business, it asserts that a new Windows Resiliency Initiative includes Quick Machine Recovery as a key capability. Very interesting!
Explaining Windows Resiliency Initiative Includes Quick Machine Recovery
This new initiative “takes four areas of focus” as its goal — namely (all bullet points quoted verbatim from the afore-linked blog post, except for my [bracketed] commentary):
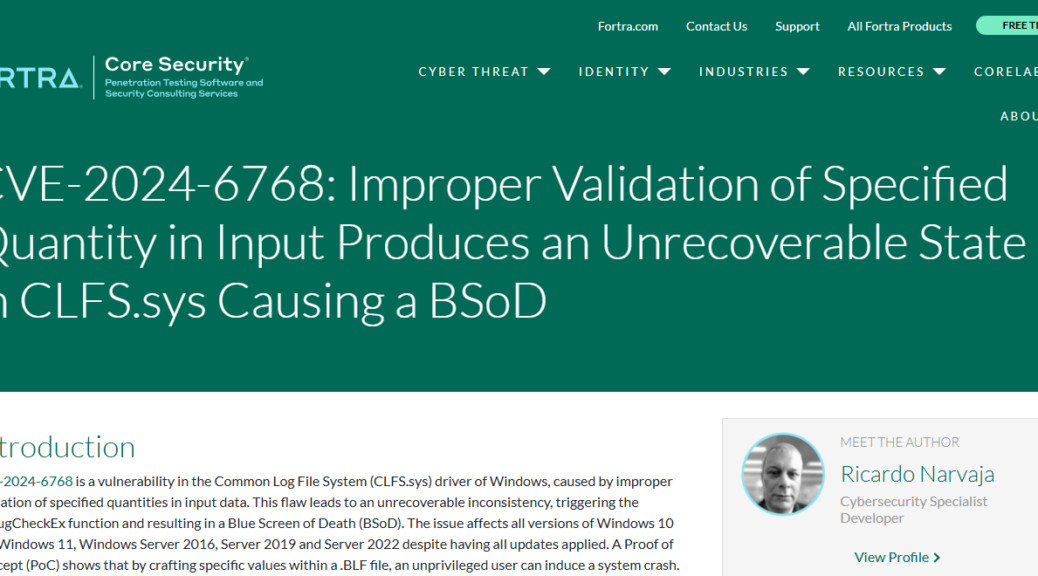
- Strengthen reliability based on learnings from the incident we saw in July. [Crowdstrike kernel mode error took down 8.5M Windows PCs.]
- Enabling more apps and users to run without admin privileges.
- Stronger controls for what apps and drivers are allowed to run.
- Improved identity protection to prevent phishing attacks.
The first and arguably most impactful preceding item is what led MS to its announcement of Quick Machine Recovery. Here’s how Weston explains it:
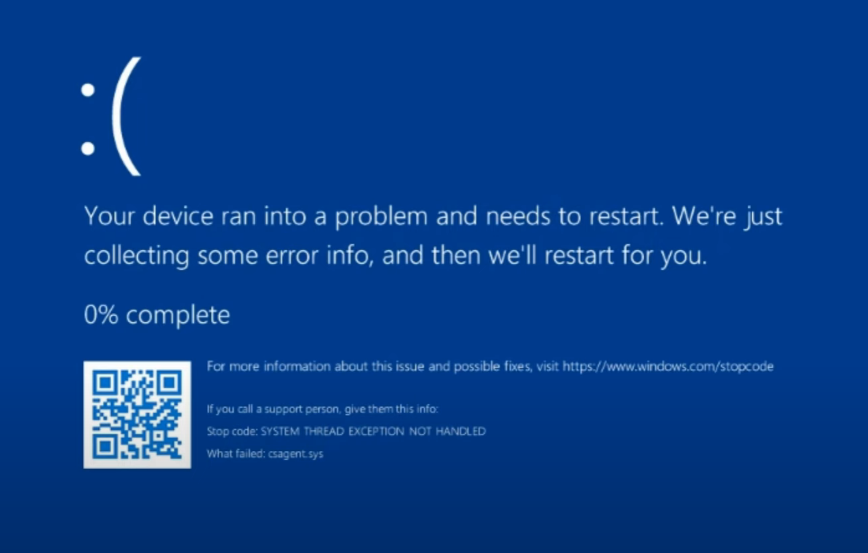
This feature will enable IT administrators to execute targeted fixes from Windows Update on PCs, even when machines are unable to boot, without needing physical access to the PC. This remote recovery will unblock your employees from broad issues much faster than what has been possible in the past. Quick Machine Recovery will be available to the Windows Insider Program community in early 2025.
In other words, this new feature should enable what savvy administrators had to do using OOB access to affected machine via KVMs smart enough to bootstrap machines otherwise unable to boot.
Great Addition: How’s the Execution?
IMO this is something MS should’ve built into Windows long ago. I’m curious to see how (and how well) it works. I’m also curious to see if it will be available for Windows 10 as well as 11. Only time will tell, but I’ll be all over this when it hits Insider Builds early next year. Good stuff — I hope!!