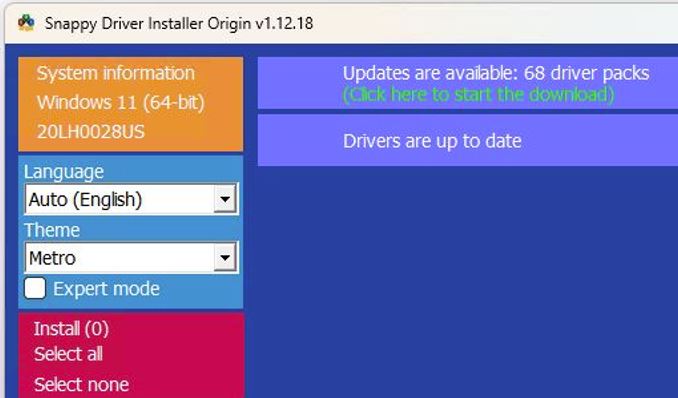
I guess it just happens every so often. Right now, Lenovo Vantage is nagging me to upgrade graphics drivers — both Intel and NVIDIA — on my 2018 Vintage Thinkpad X1 Extreme. (Internals: i7-8850H CPU, 32 GB DDR4, NVIDIA GeForce GTX 1050 Ti, dual Samsung OEM SSDs.) But Lenovo Vantage wants me to run an Optimus display driver and GeForce Experience wants a GeForce Game Ready Driver. The back-n-forth is leading to some X1 Extreme graphics driver delirium. What’s a body to do?
Surmounting X1 Extreme Graphics Driver Delirium
In a nutshell the problem is this: when I update to the Optimus driver, GeForce tells me to update to the Game Ready Driver, When I go the other way round, that flips so Lenovo Vantage tells me to get back on its track. I don’t do a lot of heavy-duty graphics on this laptop, and I’ll be darned if I can tell any difference.
I asked Copilot: “What’s the difference between running a GeForce Game Ready Driver versus NVIDIA Optimus Display Driver on a GeForce GTX 1050 Ti with Max-Q Design?” It says: battery and easy switching between discrete and integrated GPU for Optimus, versus gaming performance and support for newest games for Game Ready Driver.
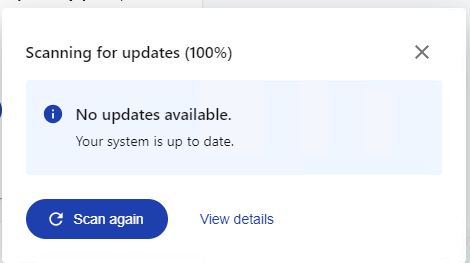
Dilemma dehorned: I don’t play games and I do switch back and forth between the Intel UHD 630 and the discrete GPU. But I had to finagle a bit to get the status from Lenovo Vantage you see above, where it tells me “No updates available.” Deets follow next…
Both Intel and Optimus Must Update
Something about the update package from Lenovo was successfully updating the GeForce driver, but failing to do the same for Intel. How could I tell? Two ways:
- The Update package did not run all the way to completion.
- The driver version for the Nvidia device matched that for the Lenovo update package (31.0.15.3770), while that for the Intel UHD 620 was lower (update version was 27.20.100.9316 but the running version ended in 8967 instead). Oops!
Because the Lenovo installer wasn’t finishing up (and the Intel Driver & Support Assistant was cheerfully oblivious), I exercised the download package’s offer to extract its contents to a folder. Then I went into Device Manager, right-clicked into “Update driver” and turned it loose on the Intel folder in the unzipped file archive that extract created for me. It took a while to complete, but this worked.
So now, I’ve got the latest Optimus drivers for my X1 Extreme and it’s all good. Here in Windows World, if you’re willing to stop and think about what you’re doing, there’s nearly always a way to fix such issues. Done!